Market Share
Worldwide Security Information and Event Management Market
Shares, 2018: By Size of Business — The Attempt to Serve All
Client Needs
Christopher Kissel
Frank Dickson
THIS IDC MARKET SHARE EXCERPT FEATURES SPLUNK
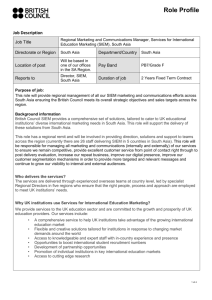
IDC MARKET SHARE FIGURE
FIGURE 1
Worldwide Security Information and Event Management 2018 Share Snapshot
Note: 2018 Share (%), Revenue ($M), and Growth (%)
Source: IDC, 2019
June 2019, IDC #US45161819e
IN THIS EXCERPT
The content for this excerpt was taken directly from Worldwide Security Information and Event
Management Market Shares, 2018: By Size of Business — The Attempt to Serve All Client Needs (Doc
# US45161819). All or parts of the following sections are included in this excerpt: Executive Summary,
Market Share, Who Shaped the Year, Market Context, Appendix and Learn More.
EXECUTIVE SUMMARY
IDC estimates that global security information and event management (SIEM) products and service
providers improved revenue by 12.4% in 2018, realizing sales of just over $3 billion. SIEM remains a
fundamental and essential cybersecurity tool. In general, the need for a SIEM becomes more
important as a company grows in size. Traditionally, SIEM platforms have been used to generate
compliance reporting, and this is true and an important function today. SIEM has also been used for
storage and indexing of packets for investigations; the hope being presently investigated alerts can be
tracked for dwell time in a network's environment. Every internet browser session, email, internal
server and router transaction, and Active Directory request generates a log. In theory, with the proper
amount of time and skill, logs could be reconstructed that they will find when the adversary entered the
network, what digital properties were exfiltrated, and what the extrusion path of the adversary was. A
fair and lively argument can be made that the intelligent collection of metadata provides an able and
cost-effective cyberdefense, but it should be noted that without 100% full-packet capture (PCAP),
reconstruction of event timelines with the original artifacts is not possible. Including forensic
capabilities, SIEM is the last hope of catching the adversary.
Naturally, the scenario of "last hope" is glum at best. Beginning in 2015, SIEM vendors made a
conscientious effort to reinvent under the banner of next-gen SIEM or SIEM 2.0. Next-gen SIEM was
the idea that SIEM could be used as the best real-time threat detection platform. This had (has) some
merit. The biggest problem in cybersecurity circa 2015 was that cybersecurity was malware signature
based and reactive. True, there are and have been threat intelligence feeds, but by and largely,
firewalls, antivirus, and endpoint protection only initiated when known malware signatures interfaced
with the technologies. The hope for SIEM was the introduction of user behavioral analytics (UBA)
would provide a backstop and a way to track low and slow zero-day threats.
Two key metrics measure the efficacy of a security operation center (SOC): mean time to detect
(MTTD) and mean time to respond (MTTR). SIEM is a log-based technology and as such can facilitate
both MTTD and MTTR. In 2019, UBA is an important addendum to an overall cybersecurity posture.
UBA is both a discrete technology and an essential technology feature set used across multiple
technologies such as endpoint detection and response, threat analytics, and SIEM. The idea is that
UBA is an analytic set that establishes individual relationships for each individual entity in the network.
The application of UBA establishes a statistical baseline that is not only a basis for deviant behavior
but can also be a "golden image" of what a device is and what it should be doing. In SIEM, UBA
(optimally) can refine and index the status of machines or identities over multiple log sources, and this
addresses the MTTD problem.
The next strong use case for SIEM is improving MTTR. If the SIEM is bidirectionally ingesting log and
flow data from multiple log sources, it stands to reason that the same connectivity can be used to fortify
the cybersecurity surface. Enter orchestration. With the proper APIs or security orchestration platform,
the SIEM can send the malware signatures associated with rule-based, role-based, risk-based, UBA
©2019 IDC
#US45161819
2
anomalies, or refined alerts by chaining these events to firewalls, endpoint, IDS/IPS, and so forth.
These can happen with or without manual intervention. Enter automation. The potential uses of
automation emanating from the SIEM are countless including writing and importing new rules to the
next-generation firewall, sending files to a sandbox, quarantining machines, or initiating workflow for
SOC analysts.
Admittedly, there is a lot to unpack here. The idea of log management and the evolving SIEM are
roughly 25 years old. In technology, software or products that last this long are rare, and that the
technology is still achieving double-digit year-over-year (YoY) growth is astounding. However, the
previous and longish explanation of the proper use of SIEM also plants the seeds of what the
competitive cybertechnology looks like. Throughout the body of this text, we will not only explain how
SIEM platforms are differentiated from each other but also explain in part the larger concerns for SIEM
as a larger set of technology against other cybersecurity approaches.
This IDC study provides the market share data for worldwide security information and event
management by size of business.
"Right now, SIEM enjoys a central and crucial role in the overall cybersecurity postures of
organizations," observes Chris Kissel, research director, Worldwide Cybersecurity Products for IDC.
"However, SIEM vendors will be vexed to meet the emerging needs of Internet of Things (IoT) and
heterogeneous networks. And while SIEM provides unique visibility and facilitates orchestration with
other cybersecurity platforms, SIEM vendors will be challenged by security analytics platform
providers, endpoint detection and response (EDR), and open source platforms to hold onto market
share."
ADVICE FOR TECHNOLOGY SUPPLIERS
In this document, we are using SIEM as a unifying term for platforms that ingest different logs and
flows, have dashboards specifically used for threat investigation and begin remediation, and are
capable of compliance reporting. In reality, form factors can change the value proposition SIEM. SIEM
as a service (cloud based), heterogeneous environments (a mix of public cloud, private cloud, and onpremises), and on-premises SIEM with PCAP retention are dramatically different. While SIEM vendors
have slightly different approaches depending upon the size of business of their clients, the following
attributes the vendors must provide to win and maintain business are universal. These would be the
value propositions that SIEM vendors have to explain to perspective buyers:
Explain pricing up front. IDC appreciates that this is no casual request. Even two parties acting
in good faith may not understand what is in a given network until an appliance is fully installed
or service initiated. Customers do not need to know if the license is event or messages per
second driven (most common), by appliance or collectors/forwarders, or enterprise licenses for
a set term. The vendor should also explain what happens when a customer reaches capacity
or how the vendor will support burst usage (like online retailers at Christmas).
Decide what the storage needs are. In some on-premises instances, the customer will be
collecting full packets and storing them on-premises. However, IDC believes it is incumbent on
the SIEM vendor to suggest traffic shaping technologies like Gigamon and Ixia when metadata
collection is appropriate or when cold storage suffices.
Map out how a SIEM will work in the potential customer's environment. The largest SIEMs like
Splunk, IBM, Micro Focus, LogRhythm, RSA, and McAfee will be widely integrated with the
leading firewalls, endpoint protection, EDR, and IDS/IPS service providers. While it is likely the
©2019 IDC
#US45161819
3
cost of a third-party technology will not be affected by a SIEM license, whether or not an
appliance is a fully fledged integration module or APIs are developed over OpenAPI adds cost
and time to stand up devices.
Ask about the SIEM's capabilities in emerging environments. Traditionally, SIEM is not an
important tool in DevOps environments because containers are spun up and taken down for
purpose-built, temporal workloads. However, purpose-built workloads are likely becoming
more prevalent as IoT is taking shape. Speaking of IoT, the vendor needs to articulate its
strategy for tracking IoT devices from either an identity or security standpoint within its SIEM.
Account for public cloud environments. Much of what needs to be done with public cloud
collection is being addressed by the public cloud providers themselves in terms of certifying
platforms. The Microsoft VTAP helps all security point products. The majority of SIEM have
ways to collect flows from popular SaaS application like Office365 and Salesforce.
Acknowledge that soft costs are costs. Any number of factors can escalate the total cost of
owning a SIEM quickly. As mentioned, the quality of APIs is a factor; a vendor has to be
transparent in how much support it will lend in writing scripts or at least in providing libraries.
Not all security analysts are equal. While maintenance and support are usually sold as a
supplement to the software (and generally at about 20% of the overall cost of the
software/service), hours of tech support should be stated up front.
Offer threat detection and more. Competing against SIEM are companies that make use of
analytics for business intelligence. Analytics-based companies are at ease with "if then, what"
scenarios. If a breach has been fully remediated, the SIEM may either want to have attack
simulation capabilities or be able to hypothesize what given threats in the wild might do to a
network (recent examples include WannaCry and Petya). Different platforms and some SIEM
are able to use network traffic analysis as indicators of compromise (IOC), but even if a
network bottleneck is not a security problem, it cannot hurt to notify the IT team just the same.
Ask how to get SaaSy. An emerging cybertechnology is MDR. MDR companies like ArcticWolf
and eSentire collect your logs, offer unlimited storage, and give an SLA for reporting and
responding to alerts. A space exists between traditional SIEM and MDR where a company
may want to do its own threat response and storage but wants the SIEM vendor to handle
alerts and the architecture of the cybersecurity posture.
Recognize that it's not your fault, it's mine. The famous breakup line is oddly applicable to
SIEM vendors. Customers are becoming put-off by the prospect of vendor lock-in. While it
feels like SIEM vendors might hope to be a bit opaque about what happens at the end of a
contract, in the long run, a mature discussion about what happens to encrypted files, PKI keys,
identities, and stored packets likely wins business in the first place and generates renewals
down the road.
MARKET SHARE
Table 1 presents the market share data for 22 separate vendors in terms of overall revenue for
calendar years 2017 and 2018, year-over-year change, and then for business segments — 1–999
employees, 1,000–2,499 employees, 2,500–9,999 employees, and 10,000+ employees. These figures
represent the size of the purchasing company and not the buying centers.
Figure 2 presents the analysis of the top 5 companies' competitive environments in the 10,000+
employees business segment as well as some of the smarter vendor offerings. Splunk, LogRhythm,
and Alert Logic are responsible for the majority of new dollars won in SIEM. What is hard to tell is how
much of current trending is due to marketing or usability.
©2019 IDC
#US45161819
4
TABLE 1
Worldwide Security Information and Event Management Revenue by Vendor and by
Size of Company, 2017 and 2018
Revenue ($M)
Revenue by Number of Employees ($M)
Company
2017
2018
2017–2018
Growth (%)
1–999
employees
1,000–2,499
employees
2,500–9,999
employees
10,000+
employees
Splunk
433.5
596.6
37.6
13.8
63.8
220.7
298.2
IBM
530.7
568.9
7.2
5.7
45.5
199.1
318.6
Micro Focus (ArcSight)
345.1
298.0
-13.7
3.0
8.9
152.0
134.1
LogRhythm
174.6
208.1
19.2
15.6
54.6
65.0
72.8
RSA (EMC) Dell
119.6
135.9
13.6
4.1
17.7
40.1
74.0
Other
1084.4
1213.0
11.9
128.4
290
446.1
348.7
Total
2,687.9
3,020.5
12.4
170.6
480.5
1,123.0
1,246.4
Source: IDC, 2019
©2019 IDC
#US45161819
5
FIGURE 2
Worldwide Security Information and Event Management Revenue Share by Vendor
with 10,000+ Employees, 2018
Source: IDC, 2019
The enterprise SOC environment is differentiated by the size of budgets and the skill of its analysts
(which is not to diminish analysts from smaller companies). However, enterprises have enough budget
to have positions like "a SIEM specialist" and frequently augment their talent pool by raiding smaller
companies. This means that these SOCs will likely have more tools to integrate; IDC has heard of
SOCs that have as many as 100 tools at its disposal.
Familiarity and usability are important factors in the enterprise SOC. It stands to reason that
orchestration and automation are more important considerations with enterprises with something like
30 tools rather than in large business or midsize SOC that might have 10–15 different tools. IDC
believes that IBM Resilient has helped IBM gradually increase its enterprise business and Splunk's
tight integration with Phantom has been a key factor in Splunk's rapidly expanding SIEM presence.
However, there is an inherent conundrum in enterprise SIEM. While accepting multiple log sources
can help uncover threat vectors that malware signatures alone may not, data ingestion and storage
come with costs. The company that is most cited for its consumption model is Splunk. IDC thinks that
there will be a general migration away from consumption-based SIEM, but it is important to note that
there is no evidence that this is currently affecting Splunk.
Exabeam is proving to be a worthy challenger as an enterprise SIEM. Exabeam built its reputation as a
UBA analytics provider, but currently it is gaining licenses as both a SIEM supplement and a SIEM
replacement. Exabeam SIEM is offered as SIEM SaaS and on-premises. This allows Exabeam to
©2019 IDC
#US45161819
6
dynamically change its platform and push new protection from one to many. Importantly, Exabeam
charges by the user and not by the log sources or consumption.
In its current iteration, Exabeam ingests over 200 log sources. Exabeam has a well-defined indexing
hierarchy using 2,500 parsers. The parsing of data allows real-time visibility as the log source
assembled in real time and analyzed on the Smart Timelines platform. The Smart Timelines uses the
MITRE ATT&CK framework, meaning that much of the investigatory stages are preassembled in the
SIEM.
For obvious reasons, enterprise SIEM is hotly contested. When all of the broth is boiled off, the most
important that any security tool provider can provide is MTTD and MTTR. When expense becomes a
lesser factor, SIEM competes against other SIEM, security threat analytics providers like Darktrace
and Anomali, and managed service security providers (MSSP). Pertaining to EDR, SIEM is more likely
to be viewed as a complement to EDR rather than a competitor.
The SIEM providers have to compete on a platform level, against each individual component within a
SIEM, and have capabilities appreciably better than what can be done on open platforms to win
accounts for businesses with 2,500–9,999 employees (see Figure 3). Some of the practical scenarios
for competition include:
Managed and professional services. Generally, MSSPs are too expensive, and large
companies may be uncomfortable outsourcing its IT, but MSSPs are in play.
MDR. MDR offers alert management and SLAs on alerts. This is an attractive alternative or at
least a viable augmentation to the SOC.
Hybrid SOC architectures. To cut corners, it is possible that a SOC will use elements of the
open source Elasticsearch, Logstash, and Kibana (ELK) stack. Conceivably, a SOC could use
public cloud or network-attached storage (NAS) for storage, Elasticsearch, and Bro for threat
detection and bypass SIEM altogether.
Data management platforms in security. Cloudera has an effective use case. Developers can
use RegEx, Python, or Scala for on-demand compute. The data is stored in such a way that
data scientists can test hypotheses on the platform without disturbing the workflow.
Threat detection platforms. The ability to visualize threats still matters in these SOCs.
Companies of this size are not against using a SIEM for log collection but are using a security
analytics platform like Vectra or Darktrace for visualization or UBA.
©2019 IDC
#US45161819
7
FIGURE 3
Worldwide Security Information and Event Management Revenue Share by Vendor
with 2,500–9,999 Employees, 2018
Source: IDC, 2019
Just out of the shear enormity of its revenue, IDC believes that Splunk still leads in revenue for
businesses with 1,000–2,499 employees (see Figure 4). LogRhythm is a contender, and ultimately
Alert Logic and AlienVault (now AT&T) are poised to gain market share in 2019.
The competitive drivers are much the same for business bound by 2,499 as they are for 9,999 with two
notable exceptions. For midsize businesses, cloud hosts are potentially disruptive to SIEM. For
instance, AWS provides two events per second (EPS) log storage as a part of its hosting agreement.
Naturally, Azure provides Active Directory services in its cloud. In November 2018, AWS announced
better granularity for access permissions to cloud, meaning SaaS applications are less leaky. The
longer fear is that the public cloud providers will augment their host environment with threat detection.
(Well actually, this is happening.) In February 2019, Microsoft announced its Microsoft Azure Sentinel
cloud-based SIEM. Amazon GuardDuty monitors its cloud environments to look for anomalous
behavior.
EDR becomes a viable alternative to SIEM especially in this market vertical. While SIEM takes a
systemswide perspective of what happens on a network, EDR providers have endpoint visibility. EDR
has direct access to memory and can detect device manipulation on the device rather than trying to
assess telemetry back on the SIEM.
©2019 IDC
#US45161819
8
FIGURE 4
Worldwide Security Information and Event Management Revenue Share by Vendor
with 1,000–2,499 Employees, 2018
Source: IDC, 2019
That a company is small does not mean it is inconspicuous to the nefarious miscreant. Besides, many
larger companies have buying subcenters for regional offices. And regardless of size, personally
identifiable information (PII) or credit card numbers are just as valuable when stolen from these
companies.
In terms of scale and footprint, the largest SIEM platforms are IBM QRadar and RSA NetWitness,
which are not affordable by businesses of this size. These companies are limited by the number of
cybersecurity technologies they can buy as well as the number of dedicated security personnel that
are dedicated to security. It is likely that IT personnel double up as security.
The approach to incident response is simply different with smaller organizations (see Figure 5). It is
easier and more expedient to have disaster recovery protocols than it is to reimage or patch machines.
Up into mid-2017, SIEM vendors built all-in-one physical appliances that protected servers inline.
LogRhythm had an all-in-one device, and AlienVault supported the Unified Security Management
(USM) appliance. While these appliances still exist, even AlienVault is placing its energies into cloud.
A significant element of the smaller businesses is the sense of community, and AlienVault OSSIM
(Open Source SIEM) and SolarWinds with its THWACK network share data and tactics among users.
©2019 IDC
#US45161819
9
Alert Logic is the likely leader of SIEM for businesses with 1-999 employee, and we expect AlienVault
to gain ground. A dark horse in this category may be SolarWinds Securonix, which can scale to
smaller deployments.
FIGURE 5
Worldwide Security Information and Event Management Revenue Share by Vendor
with 1–999 Employees, 2018
Source: IDC, 2019
WHO SHAPED THE YEAR
As mentioned in the Executive Summary section, SIEM vendors compete against SIEM vendors
internally and managed detection and response companies, data and business intelligence firms, and
open source platforms externally. While the competitive environment is intense, the SIEM vendors in
the sections that follow are ahead of the curve at least for now.
Splunk
An interesting statistic released by Splunk comes from the report The State of Dark Data. On average,
55% of data is collected and stored and never surfaced again. If nothing else, Splunk has always been
like an attendant cook insisting on use every morsel of food for stew — for Splunk, unused data is
unused potential.
At Splunk.conf 2018, toward security, Splunk announced the following enhancements:
©2019 IDC
#US45161819
10
Splunk Enterprise Security (ES) 5.2. The announcement of "event sequencing" was an
important improvement to Splunk ES 5.2. Splunk ES can process a series of notable events
and correlate with risk modifiers to reduce the number of alerts and give SOC analysts visibility
into the type of attack that is occurring.
Phantom 4.1. The depth of the Phantom orchestration platform is impressive — the platform
supports 230 apps and supports 1,200 API callouts. Another key feature of Phantom is an
abstraction layer — meaning, if a company decides to go from a Cisco NGFW firewall to a Palo
Alto firewall, the client can install the new firewall without having to rewrite its existing
automation playbooks.
Splunk UBA 4.2. In the majority of attacks, at some point the miscreant either finds the
credentials of legitimate users and/or encrypts exfiltrating data. Splunk UBA creates a version
of truth for each individual user in the network and compares real-time activity against
historical behaviors. To monitor end-user behaviors, Splunk UBA can process 80,000 events
per second and can monitor as many as 1 million devices. Finally, the new Splunk to Kafka
UBA connector sends data directly to Kafka, bypassing the search head delivering 10x faster
ingestion performance.
Splunk adaptive response framework (ARF) is the underpinning of Splunk ES. The ARF includes
integrations with over 50 security vendors. ARF includes a correlation builder, incident review, and
response audit that allows the analyst to manage workflow and double-check actions against specific
domains.
It can be argued that the best advocacy for Splunk is the many different platforms Splunk deploys for
IT and IoT and the IT admin comfortable in the user experience. In IT, Splunk has application
monitoring, infrastructure monitoring, virtualization monitoring, and predictive analytics where the
platform anticipates when different devices could use a maintenance upgrade.
One very specific use case occurred with Arizona State University. The systems admin was the
purchaser for the university and thought he would gain an economy of scale if he unified HR, network,
and other database administration on a unified Splunk platform. He was confident that data
segmentation would be handled comfortably by third-party applications and even if this did not match
perfectly, his thinking was that he would gain efficiency by having everyone from separate departments
using the same tool. His observation is that this is exactly what happened.
Splunk has consistently grown revenue 35—40% YoY for the past four years. However, its position as
the best data ingestion engine with security and analytics is being challenged by companies like
Securonix and Exabeam, which use various forms of Apache data collection (Hadoop and Kafka) and
apply an analytics layer to data lakes. SAP has its toes in water for SIEM, and even tradition BI
platforms like BMC Software could make a run at the security analytics market.
MARKET CONTEXT
Significant Market Developments
The competitive, technical, and marketing concerns germane to SIEM vendors have been addressed
throughout the document, but there remain a few notes of interest.
Until recently, automation and orchestration platforms have been either standalone or an essential
element of SIEM. In 2016, Rapid7 purchased Kommand. In 2017, IBM purchased Resilient for
orchestration in incident response, and in April 2018, Splunk purchased Phantom. In February 2019,
©2019 IDC
#US45161819
11
Palo Alto Networks announced its intention and has since purchased Demisto. This is an interesting
development in the field of cybersecurity. In 2018, Palo Alto Networks acquired Secdo, Evident.io, and
Redlock to gain EDR capabilities and cloud visibility. Palo Alto Networks now boasts robust threat
detection capabilities in WildFire malware detection and Cortex XDR for endpoint and network traffic
analysis. Can companies like Tenable and Qualys be far behind in unifying disparate technology
capabilities? In addition, will automation and orchestration platforms become more like UBA platforms
that are underlying, almost commodity technologies, playing a supporting role in security analytics,
EDR, and SIEM? Likely, a couple of cybersecurity items are still in spin, and they may lessen or
promote the importance of SIEM. IDC expects that cyberinsurers are going to have an almost
precursory checklist of requirements for assurance. The checklist may look like this:
The insured may deduct 5% from its premium if it follows the MITRE ATT&CK Framework.
The insured may deduct 7% from its premium if it follows the NIST 800.53 requirements of
monthly reporting of all of its digital assets and appliances.
The insured may deduct 10% from its policy if it can demonstrate an average time of 24 hours
to respond to critical alerts.
The second overriding concern is government regulators. GDPR and the upcoming California Privacy
Laws are being implemented. The degree to which these regulators can assess fines and what
recourse companies have is still being established. While the majority of the focus has been on identity
and data sovereignty, the degree to clear negligent cybersecurity practices contribute to a breach has
not been openly litigated yet.
METHODOLOGY
The IDC software market sizing and forecasts are presented in terms of commercial software revenue.
IDC uses the term commercial software to distinguish commercially available software from custom
software. Commercial software is programs or codesets of any type commercially available through
sale, lease, rental, or as a service. Commercial software revenue typically includes fees for initial and
continued right-to-use commercial software licenses. These fees may include, as part of the license
contract, access to product support and/or other services that are inseparable from the right-to-use
license fee structure, or this support may be priced separately. Upgrades may be included in the
continuing right of use or may be priced separately. Commercial software must be available for
competitive bidding. These use cases are counted by IDC as commercial software revenue.
Commercial software revenue excludes service revenue derived from training, consulting, and
systems integration that is separate (or unbundled) from the right-to-use license but does include the
implicit value of software included in a service that offers software functionality by a different pricing
scheme. It is the total commercial software revenue that is further allocated to markets, geographic
areas, and sometimes operating environments. For further details, see IDC's Worldwide Software
Taxonomy, 2018: Update (IDC #US44835319, February 2019).
Bottom-up/company-level data collection for the calendar year 2018 began in January 2019, but there
was a previous round of collection beginning in September 2018 for the calendar year 2017. The
surveys asked the vendors to provide revenue by client size of business, form factor, geographic
region, and vertical market (presented in this study are overall market share and size of business). The
size of business was for overall size of business and not individual buying centers. The survey data
was the largest overriding factor in the revenue presented here; however, public reporting from 10-Q
©2019 IDC
#US45161819
12
and 10-K statements were considered as was IDC Software Tracker data. Not all companies provided
direct feedback, and IDC will not comment on specific companies.
The data presented in this study is IDC estimates only.
Note: All numbers in this document may not be exact due to rounding.
MARKET DEFINITION
Security intelligence and event management (SIEM) solutions include products designed to aggregate
data from multiple sources to identify patterns of events that might signify attacks, intrusions, misuse,
or failure. Event correlation simplifies and speeds the monitoring of network events by consolidating
alerts and error logs into a short, easy-to-understand package. Products can also consolidate and
store the log data that was processed by the SIEM. This submarket also includes products that collect
and disseminate threat intelligence, provide early warning threat services, and can provide information
on countermeasures. The data from SIEM products is provided to policy and compliance solutions for
consistent reporting.
The formal definition of SIEM here is important for a couple of reasons and mostly for the reason of
providing transparency. This term feels imprecise, but one of the criterions for a platform to be
considered a SIEM is that it has to drive like a SIEM. A SIEM must take in different logs and flows, has
dashboards specifically used for threat investigation, and is capable of compliance reporting. In this
sense, a SIEM is differentiated from security analytics products that are designed to allow users
flexibility in specifying their particular security framework and running data against that framework in
order to better analyze data; examples would include Darktrace and Anomali. And SIEM is different
than threat intelligence products that are designed to take in a variety of threat intelligence sources
and provide a platform for organizations to analyze their own data against a variety of different threat
intelligence feeds. Often, companies will use business intelligence (BI) platforms in combination with
open source platforms to index data, but IDC does not count this as SIEM revenue. Ideally though, a
SIEM incorporates aspects of security and threat analytics, threat intelligence, business intelligence,
and database management to provide search, storage, indexing, and most importantly data that
facilitates incident detection and response.
RELATED RESEARCH
IDC Market Glance: Cybersecurity AIRO, 1Q19 (IDC #US44774119, February 2019)
Market Analysis Perspective: Worldwide Cybersecurity AIRO, 2018 - Harden, Detect,
Respond, and Repeat (IDC #US44282118, September 2018)
Worldwide IT Security Products Forecast, 2018-2022: Do You Make Friends or Acquire
Technology to Round Out a Portfolio? (IDC #US44182918, August 2018)
Worldwide Security and Vulnerability Management Forecast, 2018-2022: SVM Vendors Fight
Off New Market Entrants (IDC #US43491618, July 2018)
Worldwide Security and Vulnerability Management Market Shares, 2017: Defending the
Boundaryless Network (IDC #US42049417, July 2018)
Worldwide Security as a Service Market Shares, 2017: The Sweet Spot Between DIY and
Managed Services (IDC #US44016818, June 2018)
©2019 IDC
#US45161819
13
About IDC
International Data Corporation (IDC) is the premier global provider of market intelligence, advisory
services, and events for the information technology, telecommunications and consumer technology
markets. IDC helps IT professionals, business executives, and the investment community make factbased decisions on technology purchases and business strategy. More than 1,100 IDC analysts
provide global, regional, and local expertise on technology and industry opportunities and trends in
over 110 countries worldwide. For 50 years, IDC has provided strategic insights to help our clients
achieve their key business objectives. IDC is a subsidiary of IDG, the world's leading technology
media, research, and events company.
Global Headquarters
5 Speen Street
Framingham, MA 01701
USA
508.872.8200
Twitter: @IDC
idc-community.com
www.idc.com
Copyright Notice
This IDC research document was published as part of an IDC continuous intelligence service, providing written
research, analyst interactions, telebriefings, and conferences. Visit www.idc.com to learn more about IDC
subscription and consulting services. To view a list of IDC offices worldwide, visit www.idc.com/offices. Please
contact the IDC Hotline at 800.343.4952, ext. 7988 (or +1.508.988.7988) or sales@idc.com for information on
applying the price of this document toward the purchase of an IDC service or for information on additional copies
or web rights.
Copyright 2019 IDC. Reproduction is forbidden unless authorized. All rights reserved.