Improving the Security of EMV Contactless Payments Protocol Analysis Aims
advertisement
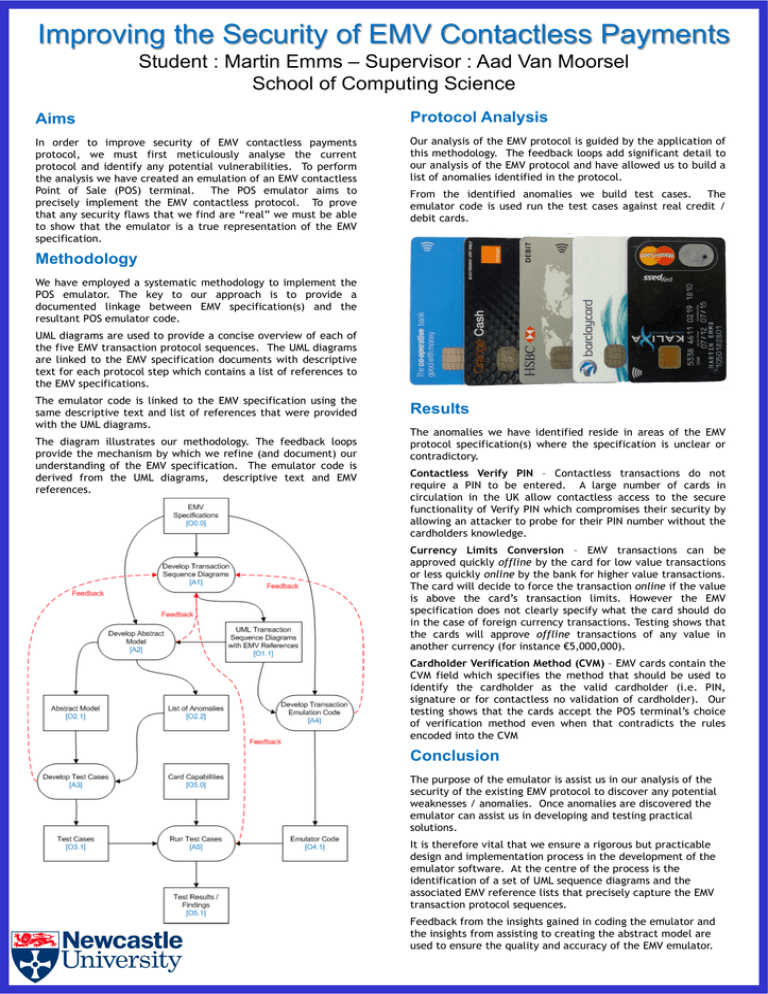
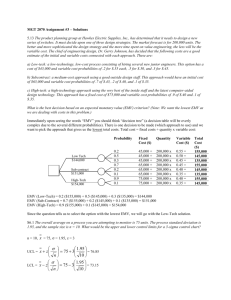
Improving the Security of EMV Contactless Payments Student : Martin Emms – Supervisor : Aad Van Moorsel School of Computing Science Aims Protocol Analysis In order to improve security of EMV contactless payments protocol, we must first meticulously analyse the current protocol and identify any potential vulnerabilities. To perform the analysis we have created an emulation of an EMV contactless Point of Sale (POS) terminal. The POS emulator aims to precisely implement the EMV contactless protocol. To prove that any security flaws that we find are “real” we must be able to show that the emulator is a true representation of the EMV specification. Our analysis of the EMV protocol is guided by the application of this methodology. The feedback loops add significant detail to our analysis of the EMV protocol and have allowed us to build a list of anomalies identified in the protocol. From the identified anomalies we build test cases. The emulator code is used run the test cases against real credit / debit cards. Methodology We have employed a systematic methodology to implement the POS emulator. The key to our approach is to provide a documented linkage between EMV specification(s) and the resultant POS emulator code. UML diagrams are used to provide a concise overview of each of the five EMV transaction protocol sequences. The UML diagrams are linked to the EMV specification documents with descriptive text for each protocol step which contains a list of references to the EMV specifications. The emulator code is linked to the EMV specification using the same descriptive text and list of references that were provided with the UML diagrams. The diagram illustrates our methodology. The feedback loops provide the mechanism by which we refine (and document) our understanding of the EMV specification. The emulator code is derived from the UML diagrams, descriptive text and EMV references. Results The anomalies we have identified reside in areas of the EMV protocol specification(s) where the specification is unclear or contradictory. Contactless Verify PIN – Contactless transactions do not require a PIN to be entered. A large number of cards in circulation in the UK allow contactless access to the secure functionality of Verify PIN which compromises their security by allowing an attacker to probe for their PIN number without the cardholders knowledge. Currency Limits Conversion – EMV transactions can be approved quickly offline by the card for low value transactions or less quickly online by the bank for higher value transactions. The card will decide to force the transaction online if the value is above the card’s transaction limits. However the EMV specification does not clearly specify what the card should do in the case of foreign currency transactions. Testing shows that the cards will approve offline transactions of any value in another currency (for instance €5,000,000). Cardholder Verification Method (CVM) – EMV cards contain the CVM field which specifies the method that should be used to identify the cardholder as the valid cardholder (i.e. PIN, signature or for contactless no validation of cardholder). Our testing shows that the cards accept the POS terminal’s choice of verification method even when that contradicts the rules encoded into the CVM Conclusion The purpose of the emulator is assist us in our analysis of the security of the existing EMV protocol to discover any potential weaknesses / anomalies. Once anomalies are discovered the emulator can assist us in developing and testing practical solutions. It is therefore vital that we ensure a rigorous but practicable design and implementation process in the development of the emulator software. At the centre of the process is the identification of a set of UML sequence diagrams and the associated EMV reference lists that precisely capture the EMV transaction protocol sequences. Feedback from the insights gained in coding the emulator and the insights from assisting to creating the abstract model are used to ensure the quality and accuracy of the EMV emulator.