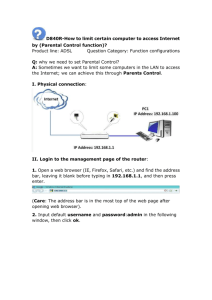
Addressing
advertisement

Addressing
Jennifer Rexford
Advanced Computer Networks
http://www.cs.princeton.edu/courses/archive/fall06/cos561/
Tuesdays/Thursdays 1:30pm-2:50pm
Goals of the Course
• Study networked systems
– Large in size and scope
– Heterogeneous components
– Decentralized control
• Explore design trade-offs
– Scalability, performance, reliability, flexibility, …
• And design principles
– Layering, end-to-end argument, late binding,
hierarchy, randomization, indirection, caching, …
• Today’s class: addressing
What is Addressing?
• Providing suitable identifiers to nodes
– So you can direct data to a node
– So you know which node sent the data
– … and how to send data back to that node
• Addressing in the U.S. mail
– Zip code: 08540
– Street: Olden Street
– Building on street: 35
– Room in building: 306
– Name of occupant: Jennifer Rexford
???
Phone Numbers
• Hierarchical
– Country code (1)
– Area code (609)
– Local exchange (258)
– Subscriber number (5182)
• Some exceptions
– 800: indirection service (free for the caller)
– 900: indirection service (billed to the caller)
– Cell phone numbers, where the node is mobile
– ... blurring distinction between name and address
Overview of Today’s Lecture
• Two widely-used addressing schemes
– Medium Access Control (MAC) addresses
– Internet Protocol (IP) addresses
• Key concepts in addressing
– Number of unique addresses
– Allocating addresses to nodes
– Flat vs. hierarchical structure
– Persistent vs. temporary identifiers
– Handling diminishing address space
– Spoofing of source addresses
• Discussion of the Cerf/Kahn 1974 paper
Some Questions
• Could every host on the Internet have an
arbitrary, unique numerical address?
– Would it scale?
• If hierarchy is necessary, how to do it?
– Tying the addressing to the topology & routing?
– What about mobile hosts? Temporary addresses?
• Who should allocate the addresses?
– Network provider? Device manufacturer?
• Does the sender of the traffic need to
authenticate itself? The destination?
– What about spoofing and impersonation?
Comparing MAC and IP Addresses
MAC
Assignment
IP
Size
Hard-coded in
the adaptor
48 bits
Configured or
learned
32 bits (in v4)
Structure
Flat
Hierarchical
Portability
Constant over life
of the adapter
Delivery within a
single network
Changes with
time and location
Delivery across
an inter-network
Purpose
E.g., social security number vs. postal address
MAC Addresses
MAC Addresses
• Flat name space of 48 bits
– Typically written in six octets in hex
– E.g., 00-15-C5-49-04-A9 for my Ethernet
• Organizationally unique identifier
– Assigned by IEEE Registration Authority
– Determines the first 24 bits of the address
– E.g., 00-15-C5 corresponds to “Dell Inc”
• Remainder of the MAC address
– Allocated by the manufacturer
– E.g., 49-04-A9 for my Ethernet card
Scalability Challenges
• MAC addresses are flat
– Multiple hosts on the same network
– No relationship between MAC addresses
• Data plane
– Forwarding based on MAC address
– Table size? Look-up overhead?
• Control plane
– Determining where the host is located
– Keeping the information up-to-date
Forwarding Frames to Destination Adapter
• Shared media
– Forward all frames on the shared media
– Adapter grabs frames with matching dest address
host
host ...
• Multi-hop switched networks
– Flood every frame over every link?
– Learn where the MAC address is located?
host
host
host
host
host
When to Learn?
• When the adapter connects to the network?
– Requires adaptor to register its presence
– Overhead even when not sending/receiving
– Leading to control messages and large tables
• When the adapter sends a frame?
– Source MAC address is in the frame
– Allows switch to learn about the adapter
• When the adapter needs to receive a frame?
– Destination MAC address is in the frame
– Switch needs to figure out how to get there
Motivation For Self Learning
• Switches forward frames selectively
– Forward frames only on segments that need them
• Switch table
– Maps dest MAC address to outgoing interface
– Goal: construct the switch table automatically
B
A
C
switch
D
Self Learning: Building the Table
• When a frame arrives
– Inspect the source MAC address
– Associate the address with the incoming interface
– Store the mapping in the switch table
– Use a TTL field to eventually forget the mapping
Switch learns
how to reach A.
B
A
C
D
Self Learning: Handling Misses
• When frame arrives with unfamiliar dest
– Forward the frame out all of the interfaces
– … except for the one where the frame arrived
– Hopefully, this case won’t happen very often
Switch floods frame
that is destined to C.
B
A
C
D
Switch Filtering/Forwarding
When switch receives a frame:
index switch table using MAC dest address
if entry found for destination
then {
if dest on segment from which frame arrived
then drop the frame
else forward the frame on interface indicated
}
else flood
forward on all but the interface
on which the frame arrived
MAC Addresses
• Disadvantages
– Large forwarding tables in the data plane
– Flooding overhead to learn location information
– Lack of privacy
• Advantages
– Persistent identifier (well, except for spoofing)
– Mobile hosts are easy to handle
– Forwarding-table look-up is a simple match
COS 461: Internet Control Protocols (#8)
• Dynamic Host Configuration Protocol (DHCP)
– End host learns how to send packets
– Learn IP address, DNS servers, and gateway
• Address Resolution Protocol (ARP)
– Others learn how to send packets to the end host
– Learn mapping between IP and MAC addresses
??? 1.2.3.7 1.2.3.156
host
host ...
DNS
host
host ...
DNS
5.6.7.0/24
1.2.3.0/24
1.2.3.19
router
router
router
COS 461: Hubs and Switches (#11)
• Different devices switch different things
– Physical layer: electrical signals (repeaters, hubs)
– Link layer: frames (bridges, switches)
– Network layer: packets (routers)
• Key ideas in switches
– Self learning of the switch table
– Cut-through switching
– Spanning trees
• Virtual LANs (VLANs)
Frame Packet TCP
header header header
User
data
Application gateway
Transport gateway
Router
Bridge, switch
Repeater, hub
IP Addresses
IP Addressing: Scalability Through Hierarchy
• Hierarchy through IP prefixes
– Routing between networks
– Allocation of address blocks
• Non-uniform hierarchy
– More efficient address allocation
– More complex packet forwarding
• Dealing with limited address space
– Larger address space (IPv6 with 128 bits)
– Sharing a small set of addresses (NAT)
– Dynamic assignment of addresses (DHCP)
Grouping Related Hosts
• The Internet is an “inter-network”
– Used to connect networks together, not hosts
– Needs a way to address a group of hosts
host
host ...
host
host
host ...
host
LAN 2
LAN 1
router
WAN
LAN = Local Area Network
WAN = Wide Area Network
router
WAN
router
Scalability Challenge
• Suppose hosts had arbitrary IP addresses
– Then every router would need a lot of information
– …to know how to direct packets toward the host
1.2.3.4
5.6.7.8
host
host ...
2.4.6.8
host
1.2.3.5
5.6.7.9
host
host ...
2.4.6.9
host
LAN 2
LAN 1
router
WAN
1.2.3.4
1.2.3.5
forwarding table
router
WAN
router
Hierarchy Through Prefixes
• Divided into network and host portions
• 12.34.158.0/24 is 24-bit prefix (28 addresses)
12
34
158
5
00001100 00100010 10011110 00000101
Network (24 bits)
Host (8 bits)
Example IP Address and Subnet Mask
Address
12
34
158
5
00001100 00100010 10011110 00000101
11111111 11111111 11111111 00000000
Mask
255
255
255
0
Scalability Improved
• Number related hosts from a common subnet
– 1.2.3.0/24 on the left LAN
– 5.6.7.0/24 on the right LAN
1.2.3.4
1.2.3.7 1.2.3.156
host ...
host
5.6.7.8 5.6.7.9 5.6.7.212
host
host
host ...
host
LAN 2
LAN 1
router
WAN
1.2.3.0/24
5.6.7.0/24
forwarding table
router
WAN
router
Easy to Add New Hosts
• No need to update the routers
– E.g., adding a new host 5.6.7.213 on the right
– Doesn’t require adding a new forwarding entry
1.2.3.4
1.2.3.7 1.2.3.156
host ...
host
5.6.7.8 5.6.7.9 5.6.7.212
host
host
host ...
host
LAN 2
LAN 1
router
WAN
router
WAN
router
host
5.6.7.213
1.2.3.0/24
5.6.7.0/24
forwarding table
Classful Addressing (and Dotted Quad Notation)
• In the olden days…
– Class A: 0*
• Very large /8 blocks (e.g., MIT has 18.0.0.0/8)
– Class B: 10*
• Large /16 blocks (e.g,. Princeton has 128.112.0.0/16)
– Class C: 110*
• Small /24 blocks (e.g., AT&T Labs has 192.20.225.0/24)
– Class D: 1110*
• Multicast groups
– Class E: 11110*
• Reserved for future use (sounds a bit scary…)
• And then, address space became scarce…
Classless Inter-Domain Routing (CIDR)
Use two 32-bit numbers to represent a network.
Network number = IP address + Mask
IP Address : 12.4.0.0
Address
Mask
IP Mask: 255.254.0.0
00001100 00000100 00000000 00000000
11111111 11111110 00000000 00000000
Network Prefix
for hosts
Usually written as 12.4.0.0/15
CIDR = Hierarchy in Address Allocation
• Prefixes are key to Internet scalability
– Routing protocols and packet forwarding based on prefixes
– Today, routing tables contain ~150,000-200,000 prefixes
12.0.0.0/16
12.1.0.0/16
12.2.0.0/16
12.3.0.0/16
12.0.0.0/8
:
:
:
12.253.0.0/16
12.254.0.0/16
12.3.0.0/24
12.3.1.0/24
:
:
12.3.254.0/24
12.253.0.0/19
12.253.32.0/19
12.253.64.0/19
12.253.96.0/19
12.253.128.0/19
12.253.160.0/19
12.253.192.0/19
:
:
:
Obtaining a Block of Addresses
• Separation of control
– Prefix: assigned to an institution
– Addresses: assigned to nodes by the institution
• Who assigns prefixes?
– Internet Corp. for Assigned Names and Numbers
• Allocates large blocks to Regional Internet Registries
– Regional Internet Registries (RIRs)
• E.g., ARIN (American Registry for Internet Numbers)
• Allocated to ISPs and large institutions in a region
– Internet Service Providers (ISPs)
• Allocate address blocks to their customers
• Who may, in turn, allocate to their customers…
whois –h whois.arin.net 128.112.136.35
OrgName: Princeton University
OrgID: PRNU
Address: Office of Information Technology
Address: 87 Prospect Avenue
City: Princeton
StateProv: NJ
PostalCode: 08544-2007
Country: US
NetRange: 128.112.0.0 - 128.112.255.255
CIDR: 128.112.0.0/16
NetName: PRINCETON
NetHandle: NET-128-112-0-0-1
Parent: NET-128-0-0-0-0
NetType: Direct Allocation
RegDate: 1986-02-24
Longest Prefix Match Forwarding
• Forwarding tables in IP routers
– Maps each IP prefix to next-hop link(s)
• Destination-based forwarding
– Packet has a destination address
– Router identifies longest-matching prefix
– Pushing complexity into forwarding decisions
forwarding table
destination
12.34.158.5
4.0.0.0/8
4.83.128.0/17
12.0.0.0/8
12.34.158.0/24
126.255.103.0/24
outgoing link
Serial0/0.1
Are 32-bit Addresses Enough?
• Not all that many unique addresses
– 232 = 4,294,967,296 (just over four billion)
– Plus, some are reserved for special purposes
– And, addresses are allocated in larger blocks
• And, many devices need IP addresses
– Computers, PDAs, routers, tanks, toasters, …
• Long-term solution: a larger address space
– IPv6 has 128-bit addresses (2128 = 3.403 × 1038)
Short-Term Solutions: Limping Along
• Network Address Translation
(COS 461 lecture #9)
– Allowing multiple hosts to share an IP address
– IP addresses not unique and not end-to-end
138.76.29.7
10.0.0.1
NAT
10.0.0.2
inside
outside
Short-Term Solutions: Limping Along
• Dynamic Host Configuration Protocol
(lecture #8)
– Share a pool of addresses among many hosts
– Dynamically assign an IP address upon request
arriving
client
DHCP server
233.1.2.5
Growth in the Number of IP Prefixes
Internet
bust
Internet
boom
CIDR
pre-CIDR
recovery?
“A Protocol for Packet Network
Intercommunication”
(IEEE Trans. on Communications, May 1974)
Vint Cerf and Bob Kahn
Written when Vint Cerf was an assistant professor
at Stanford, and Bob Kahn was working at ARPA.
Life in the Early 1970s
• Multiple unconnected networks
– ARPAnet
– Data-over-cable
– Packet satellite (Aloha)
– Packet radio
ARPAnet
satellite net
Differences Across Packet-Switched Networks
•
•
•
•
•
Addressing
Maximum packet size
Timing for handling success/failure of delivery
Handling of lost or corrupted data
Routing, fault detection, status information, …
ARPAnet
satellite net
Where to Handle Heterogeneity?
•
•
•
•
Application process?
End host?
Packet switches?
Someplace else?
• Compatible process and host conventions
– Obviate the need to support all combinations
• Retain the unique features of each network
– Avoid changing the local network components
• Introduce the notion of a gateway
Gateways Between Different Kinds of Networks
Internetwork layer
• Internetwork appears as a
single, uniform entity
• Despite the heterogeneity
of the local networks
• Network of networks
Gateway
• “Embed internetwork
packets in local packet
format or extract them”
• Route (at internetwork
level) to next gateway
gateway
ARPAnet
satellite net
Internetwork Packet Format
internetwork header
source
dest.
local
header address address
seq. byte flag
# count field
text checksum
• Internetwork header in standard format
– Interpreted by the gateways and end hosts
• Source and destination addresses
– Uniformly and uniquely identify every host
• Ensure proper sequencing of the data
– Include a sequence number and byte count
• Enable detection of corrupted text
– Checksum for an end-to-end check on the text
Process-Level Communication
• Enable pairs of processes to communicate
– Full duplex
– Unbounded but finite-length messages
– E.g., keystrokes or a file
• Key ideas
– Port numbers to (de)multiplex packets
– Breaking messages into segments
– Sequence numbers and reassembly
– Retransmission and duplicate detection
– Window-based flow control
Differences in Max Packet Size
• Select smallest packet size as the new max?
• Coordinate to determine max size on a path?
• Enable gateway to fragment a large packet?
– Reassembly by the next gateway? The receiver?
• Design trade-offs
– Coordination overhead for identifying the max
– Overhead of sending many small packets
– Overhead of buffering packets for reassembly
Discussion
• What did they get right?
– Which ideas were key to the Internet’s success?
– Which decisions still seem right today?
• What did they miss?
– Which ideas had to be added later?
– Which decisions seem wrong in hindsight?
• What would you do in a clean-slate design?
– If your goal wasn’t to support communication
between disparate packet-switched networks
– Would you do anything differently?