At-A-Glance
Cisco ONS 15454 10-Gbps Optical
Encryption Line Card
Summary
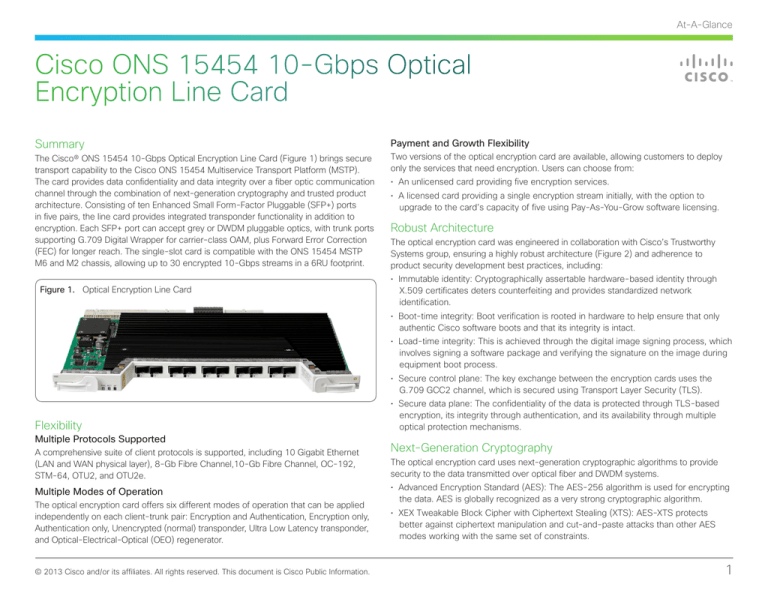
The Cisco® ONS 15454 10-Gbps Optical Encryption Line Card (Figure 1) brings secure
transport capability to the Cisco ONS 15454 Multiservice Transport Platform (MSTP).
The card provides data confidentiality and data integrity over a fiber optic communication
channel through the combination of next-generation cryptography and trusted product
architecture. Consisting of ten Enhanced Small Form-Factor Pluggable (SFP+) ports
in five pairs, the line card provides integrated transponder functionality in addition to
encryption. Each SFP+ port can accept grey or DWDM pluggable optics, with trunk ports
supporting G.709 Digital Wrapper for carrier-class OAM, plus Forward Error Correction
(FEC) for longer reach. The single-slot card is compatible with the ONS 15454 MSTP
M6 and M2 chassis, allowing up to 30 encrypted 10-Gbps streams in a 6RU footprint.
Figure 1. Optical Encryption Line Card
Payment and Growth Flexibility
Two versions of the optical encryption card are available, allowing customers to deploy
only the services that need encryption. Users can choose from:
• An unlicensed card providing five encryption services.
• A licensed card providing a single encryption stream initially, with the option to
upgrade to the card’s capacity of five using Pay-As-You-Grow software licensing.
Robust Architecture
The optical encryption card was engineered in collaboration with Cisco’s Trustworthy
Systems group, ensuring a highly robust architecture (Figure 2) and adherence to
product security development best practices, including:
• Immutable identity: Cryptographically assertable hardware-based identity through
X.509 certificates deters counterfeiting and provides standardized network
identification.
• Boot-time integrity: Boot verification is rooted in hardware to help ensure that only
authentic Cisco software boots and that its integrity is intact.
• Load-time integrity: This is achieved through the digital image signing process, which
involves signing a software package and verifying the signature on the image during
equipment boot process.
• Secure control plane: The key exchange between the encryption cards uses the
G.709 GCC2 channel, which is secured using Transport Layer Security (TLS).
Flexibility
Multiple Protocols Supported
A comprehensive suite of client protocols is supported, including 10 Gigabit Ethernet
(LAN and WAN physical layer), 8-Gb Fibre Channel,10-Gb Fibre Channel, OC-192,
STM-64, OTU2, and OTU2e.
Multiple Modes of Operation
The optical encryption card offers six different modes of operation that can be applied
independently on each client-trunk pair: Encryption and Authentication, Encryption only,
Authentication only, Unencrypted (normal) transponder, Ultra Low Latency transponder,
and Optical-Electrical-Optical (OEO) regenerator.
© 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.
• Secure data plane: The confidentiality of the data is protected through TLS-based
encryption, its integrity through authentication, and its availability through multiple
optical protection mechanisms.
Next-Generation Cryptography
The optical encryption card uses next-generation cryptographic algorithms to provide
security to the data transmitted over optical fiber and DWDM systems.
• Advanced Encryption Standard (AES): The AES-256 algorithm is used for encrypting
the data. AES is globally recognized as a very strong cryptographic algorithm.
• XEX Tweakable Block Cipher with Ciphertext Stealing (XTS): AES-XTS protects
better against ciphertext manipulation and cut-and-paste attacks than other AES
modes working with the same set of constraints.
1
At-A-Glance
Cisco ONS 15454 10-Gbps Optical
Encryption Line Card
• Galois Message Authentication Code (GMAC): GMAC is defined by National Institute
of Standards (NIST) special publication 800-38D and provides efficient ways to
authenticate a large set of data and protection against bit-flipping attacks.
Figure 2. Cisco Optical Encryption Architecture
• Elliptic Curve Diffie Hellman (ECDH): The key exchange protocol uses ECDH, providing
perfect forward secrecy as the key is never sent over the communication channel.
• Raw Source of Entropy: A NIST SP800-90 compliant true random source of entropy
is used to produce sequences of numbers that are not predictable.
• Suite-B compliant: With support for ECDSA in a future release, the Cisco optical
encryption card uses the other suite-B algorithms specified by NSA (AES, GCM,
and CDH).
Comprehensive Management
Cisco Transport Controller is a GUI-based application used to configure and manage ONS
15454 MSTP systems, including the optical encryption card. It offers these features:
• User management: Role-based access control and complete separation of privileges
between users from the transport domain and those from the security domain
• Key management: Key generation and key change interval
• Cryptographic lifecycle management: The card-to-card authentication and card
authorization between two encryption cards that must succeed prior to key exchange
• Performance management: Alarms to detect an active or a passive intrusion, as well
as the failure of any security function
Exceptional Certification and Support
Cisco Classified Network Support
Cisco offers high-touch, personalized service from a cleared team of industry-leading
network engineers dedicated to supporting Cisco’s government customers. Cisco
Classified Network Support provides expedited issue resolution to help intelligence
community agencies maintain a network primed to keep pace with mission demands.
Certifications
The optical encryption card will undergo the following government certifications to meet
mission-critical requirements.
• FIPS (Federal Information Processing Standard) 140-2 Level 2 validation
• Common Criteria NDPP (Network Device Protection Profile) compliance.
• UC-APL (Unified Capabilities Approved Products List)
Product ID: 15454-M-WSE-K9
Description: Full Feature Wire Speed Encryption Unit
System Software Required: Release 9.8
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned
are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
C45-728015-00 04/13
© 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.
2



