Försättsblad till skriftlig tentamen vid Linköpings Universitet
advertisement
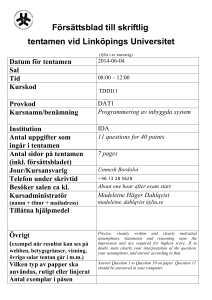
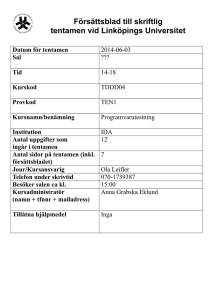
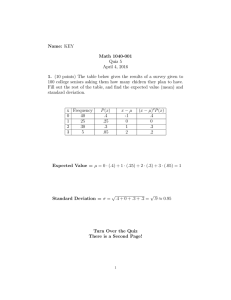
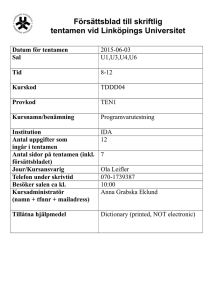
Försättsblad till skriftlig tentamen vid Linköpings Universitet (fylls i av ansvarig) Datum för tentamen Sal 2012-03-09 TER3 Tid 14-18 Kurskod TDDC32 Provkod TEN1 Kursnamn/benämning Implementation av programmodul i Java IDA 7 Institution Antal uppgifter som ingår i tentamen Antal sidor på tentamen (inkl. försättsbladet) Jour/Kursansvarig Telefon under skrivtid Besöker salen ca kl. Kursadministratör 3 (namn + tfnnr + mailadress) Johan Janzén 282490 16 Gunilla Mellheden 282297 gunilla.mellheden@liu.se Tillåtna hjälpmedel English dictionary Övrigt (exempel när resultat kan ses på webben, betygsgränser, visning, övriga salar tentan går i m.m.) Tentamen/Exam TDDC32 Design och implementering av programmodul i Java TDDC32 Design and implementation of a software module in Java 2012–03–09 14.00–18.00 • • • • No help materials are allowed, except for an English dictionary. You may answer in Swedish or English. Total number of credits is 24. Preliminary limits: 3: 12p, 4: 15p, 5: 19p. Jour (person on duty): Johan Janzén. Will visit the exam ~16.00 1. Give short answers to the following questions a) What is a and b in “(a,b)-tree”? How are they related? (1p) b) Give two examples of when a tree data structure is preferable to a hash table (1p) c) When discussing the performance of an AVL-tree, a “Fibonacci tree” is sometimes mentioned. Why is that? (1p) d) What does “Divide & Conquer” mean in an OOD context?(1p) e) What is UML?(1p) 2. a) Construct an AVL-tree from the following numbers. Show how the tree looks like after each rebalancing, as well as the finished tree. (2p) 2 5 6 3 1 4 7 b) Remove the node with the key 1. Show the resulting tree. (1p) 3. Construct a splay tree with the same number as in problem 2a. Show how the tree looks after each completed insertion. (3p) 4. The worst-case complexity of a Remove operation on a splay tree is O(n), which is quite expensive. a) Design an example of a worst-case removal. Show the tree before the removal, which node that is to be removed, and the resulting tree. Explain shortly why this is a worst-case scenario. (1p) b) Using a simple worst-case complexity analysis is considered to be unfair to the splay tree. Explain why. What kind of analysis tool should be used instead? (1p) c) An algorithm in a program is repeatedly searching for the values 1, 2, 5 in a large splay tree. Using the results from b, how long time would it take to search for these vales, given that the algorithm is searching n times (n is large)? Give a short explanation. (1p) 5. Build a skip list of the following numbers. The results from the coin tosses will be 1 tails, 1 heads, 1 tails, 2 heads, 1 tails, 3 heads, 1 tails, 4 heads... You only need to show the resulting skip list. (3p) 5 3 2 4 9 6. Insert the following keys into a hash table with an initial size of 6. The hash table uses open addressing with linear probing. The hash function is: h(k) = k mod SIZE; Rehashing should be performed as soon as the table is completely full, and will double the size of the table. Show how the table looks like before each rehash, as well as the final result after all insertions. (3p) 8 4 11 20 15 17 10 7. a) The object oriented approach to software development contains the following steps; Requirement specification, Object Oriented Analysis and Object Oriented Design. Explain the purpose of each step and how they are related to each other. (3p) b) When writing a requirement specification an important rule of thumb for the developer is “What, not how”. What does this mean and why is this important? (1p) Good Luck!