Document 12928128
advertisement

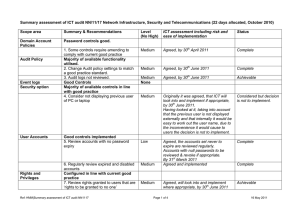
Summary assessment of ICT audit NN/11/17 Network Infrastructure, Security and Telecommunications. Update August 2011 Scope area Summary & Recommendations Domain Account Policies Password controls good. Audit Policy Event logs Security option User Accounts 1. Some controls require amending to comply with current good practice Majority of available functionality utilised. 2. Change Audit policy settings to match a good practice standard. 3. Audit logs not reviewed. Good Controls Majority of available controls in line with good practice 4. Consider not displaying previous user of PC or laptop Good controls implemented 5. Review accounts with no password expiry Ref: HMM|Summary update of ICT audit NN1117_Aug11 Level (No High) ICT assessment including risk and ease of implementation Status May 2011 Medium Agreed, by 30th April 2011 Complete Medium Agreed, by 30th June 2011 Complete Medium Agreed, by 30th June 2011 Achievable Medium Originally it was agreed, that ICT will look into and implement if appropriate, by 30th June 2011. Having looked at it, taking into account that the previous user is not displayed externally and that internally it would be easy to work out the user name, due to the inconvenience it would cause to users the decision is not to implement. Considered but decision is not to implement. Low Agreed, the accounts set never to expire are reviewed regularly. Accounts with null passwords to be reviewed & revoke if appropriate. Complete Status August 2011 Audit logs reviewed manually. Automated process in place by 30 September None Page 1 of 4 16 May 2011 Rights and Privileges 6. Regularly review expired and disabled accounts Configured in line with current good practice 7. Review rights granted to users that are ‘rights to be granted to no one’ Medium 8. Review discretionary access controls created for individual users. Medium Trusted and No trust relationships exist to allow Trusting Domains one domain to trust another domain Remote Access RAS service disabled, no RAS Service (RAS) servers within the Domain 9. Some supporting RAS services still running and one account has permission to dial in using RAS Services and Drivers Updates and Patches Logical Drives and Network Medium By 31st March 2011 Agreed and implemented Agreed, will look into and implement where appropriate, by 30th June 2011 Agreed, will look into this and implement any appropriate controls. Audit identified this as a key item, by 30th June 2011 Complete Achievable Complete Achievable Complete None Medium Agreed, we will stop service but Remote Access is not configured and no modems exist, therefore it is a very very remote threat, by 31st December 2011 Complete Low Agreed, Audit identified this as a key item, by 30th September 2011 Achievable Complete 11. Implement a patch and update process Medium Agreed, we will look into this and implement appropriate processes. Audit identified as a key item. By 30th June 2011 New deadline 31/12/11 Good progress has been made. Partially done. All important patching has a documented process. Still need training to complete task. Good Controls None 276 services available, 148 running at time of audit 10. Review regularly services running Last installed January 2010 Ref: HMM|Summary update of ICT audit NN1117_Aug11 Page 2 of 4 16 May 2011 Shares Backup Physical and Environmental Security Disaster Recovery Plan (DR) Network Topology (layout) and Resilience Network Support Network Device Security Good Controls Good Controls The plan is being worked on and requires further review to lift to current good practice 12. Include suggestions for improvement in plan None None Medium Controls adequate for council’s infrastructure as spare devices are available for single points of failure. Network team is small with good cross training in place to help ensure adequate network management resources. 13. Security alert management needs improving. None 14. Review service desk activities to identify support trends Medium Medium We consider our current processes to be suitable for our needs, although we will review the plans based on the recommendation. By 30th June 2011 The plan is being updated and will be agreed by the ICT strategy group and Business Continuity group June / July. Agreed. Implemented, critical antivirus alerts and backup messages are now configured to go to multiple staff. Agreed in part. The reports will be used within ICT for monitoring calls, but not appropriate for users, by 30th June 2011 Complete On target Complete Plan updated and approved by ICT strategy group 18th July 2011 and now available on the Intranet Complete CISCO switches which allow network connections use a weak password algorithm Ref: HMM|Summary update of ICT audit NN1117_Aug11 Page 3 of 4 16 May 2011 15. Change encryption to a stronger algorithm 16. Implement intrusion detection Remote Virtual Private Network (VPN) access Network Management and Administration Firewall Telecommunicati ons Administration Low Agreed & Implemented Complete Medium Agreed. Will look into and implement if appropriate though budget could be a barrier. Deadline is for consideration & will schedule later if appropriate. By 30th June 2011 Not realistic, new date 31st December 2011 On work program Circulated to ICT strategy group for comment and agreement May2011. To be completed by 31st October 2011 (change from 31st August 2011 in plan, as dependant on corporate strategy) Complete Available on the Intranet Good controls, a token 2-factor authentication mechanism is in place Good controls with adequate budget and resource in place. None 17. Implement a service level agreement between IT and Business areas Medium Agreed. The previous service descriptions had not been updated for some time. They have been reviewed and updated to reflect the current situation. 18. Agree a separate Network strategy Medium A network plan will be included in the ICT strategy instead of generating a separate document to minimise the number of strategies. The ICT strategy will be updated in the autumn when the new Corporate plan is agreed. Good controls noted, annual penetration tests in place Older technology used with a small amount of internal Voice-over IP. A range of Disaster Recovery options are available None Ref: HMM|Summary update of ICT audit NN1117_Aug11 None Page 4 of 4 16 May 2011