Restricting Mischievous Users in Anonymizing Networks G.Ramya ,Ms.VijiAmuthaMary
advertisement

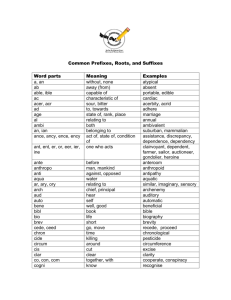
International Journal of Engineering Trends and Technology (IJETT) – Volume 9 Number 2 - Mar 2014
Restricting Mischievous Users in Anonymizing
Networks
G.Ramya1,Ms.VijiAmuthaMary2
M.E Computer Science and Engineering1, Faculty of Computer science2, Sathyabama University1, Sathyabama University2,
Chennai-600119, India
Abstract: Tor is a form of network comprised of indirect
tunnels that allows users and groups to improve their
seclusion and security on the Internet. Individuals use
Tor network to keep websites from tracking them. Then
website Administrators blocks entire network which is
connected to the abusive system to get rid of the
intruder. Hence, good users also get blocked due to this
action. So a Nymble system is developed in which
servers can “blacklist” unrefined users without
affecting good users and also sustaining secrecy across
the network. Even though Nymble System was useful
in syncing target servers with the system for an effective
reporting and countering mechanisms, it has a huge
computation overhead. So the proposed system tweak
Nymble allows users to access Internet services
privately by using a sequence of servers and proxy
repositories to hide the client’s IP address from the
target servers instead of the numerous routers based IP
hiding approach of preceding systems. These methods
ensure that the number of algorithms to sync target
servers with Nymble system is not beyond 10 thus
sinking the computation overhead. By revoking a user
for a period of time spanning multiple linkability
windows. This gives service providers more flexibility in
deciding how long to block individual users.
name. In our proposed work to do that, it requires some
changes in the design of PM. The new pseudonym
procedure needs two rounds of communication linking the
user and set of Pseudonym Managers: In the first round, the
user must prefer a random PM and connect to it directly to
demand the codename, which is a pseudonym of user’s IP
address.
A request is valid if the user IP address does not
come from a known anonymzing network and it has not
been used prior to obtaining a codename in this likability
window. The user prefers another random PM in the
second round of the pseudonym registration. The user
connects to that PM using an anonymizing network and
sends (codename, σ) pair to him. After obtaining the pair
and verifying the ring signature
the PM issues a
pseudonym that the user can use it to connect to the
Nymble Managers.if Nymble Manager goes out of service
for any reason like a a DoS attack or system crash, new
users cannot subscribe into the system and service
providers cannot extract linking token of disobedient users.
So we need more than one nymble manager
II.
Keywords: Anonymity, Pseudonymity, Unobservability,
Unlinkability
I.
INTRODUCTION
Anonymizing networks such as Crowds and Tor
direct traffic through independent nodes in detach
administrative domains to hide the originating IP address.
Anonymizing networks allows users to access Internet
services privately by using a sequence of routers to hide the
client’s IP address from the server.. Nymble system
provides all the following properties that are vital character
for successful flow of anonymization services, anonymous
authentication, backward unlinkability, biased blacklisting,
fast authentication speeds, the rate-limited anonymous
connections, and revocation auditability. Pseudonymity
means using a pseudonym as a substitute of one’s “real”
ISSN: 2231-5381
RELATED WORK:
Some of the authors of the Nymble system tried to
eliminate the role of a trusted third party (TTP). They
developed an anonymous credential system called BLAC
using a signature proof of knowledge (SPK) scheme. In this
system there is an entity called Group Manager (GM) who
is responsible for issuing credential for users. This entity
should not be considered a TTP since GM does not know
the credential of a user and hence can’t revoke user’s
privacy
In 1991, Chaum and van Heyst proposed group
signatures, wherein each member of a group can sign any
message on behalf of the group. Anyone can verify a group
signature using the group’s public key, but only a special
entity known as the Revocation Manager (RM) can
http://www.ijettjournal.org
Page 88
International Journal of Engineering Trends and Technology (IJETT) – Volume 9 Number 2 - Mar 2014
determine which group member produced a particular
group signature
IV.
PROPOSED SYSTEM:
Tsang et al proposed Blacklistable Anonymous
Credentials (BLAC) in the following year. BLAC removes
the trust assumptions from Nymble by eliminating the role
of the NM entirely. Similar to the work of Brands et al.
authentication with an SP in BLAC requires User to prove
that her credential is not present on a blacklist of revoked
credentials.
Some users all the time look to behave badly with
servers, there major objective is to make the server down.
The trouble with nymble is nymble manager blacklists a
user for one likability window (i.e.1 day), on the other day
again user can misbehave with same server or other server.
User can continue it as his everyday activity as Nymble
manager doesn’t have any means to identify such type of
users while preserving anonymity.
Schwartz et al. proposed contract-based revocation.
They leverage ideas from trusted computing to construct a
contract-based revocation system, called RECAP, using
group signatures as the underlying primitive. In particular,
they use remote attestation to allow User to confirm that
the software running on the RM will only deanonymize
user in the event that user violates a pre-agreed-upon
convention
Solution to this problem is, Pseudo Tracker is
developed as part of Pseudonym Manager in our tweak
Nymble System. Pseudo tracker contains identity
information of the user and Rating. A user registered
recently is highly rated. This rating is used to track the
users. If a user misbehaves with a server then the server
complaints to Nymble Manager (NM). NM Complaints the
picky Pseudonym to Pseudonym Manager.
Pseudo tracker
Lin and Hopper proposed Jack in late 2010. Jack
builds on the Nymble framework to weaken Nymble’s trust
assumptions. It reduces the level of trust in the VI (called
the Credential Manager (CM) in that scheme) by
eliminating the link between User’s actual identity and her
nymbles. User’s Nym (we revert to this terminology since a
pseudonym in Jack is decidedly not a verinym) in Jack is
instead based on user-chosen randomness; thus, the ZKverinym property is easily satisfied
rating
System setup
Pseudonym
manager
Sends blacklisted users
Nymble
manager
Credential Acquisition
connects
blacklist
Update
Tor network
III.
EXISTING SYSTEM:
Nymble connection
Nymble utilizes two trusted third parties (TTPs)
called the Pseudonym Manager (PM) and the Nymble
Manager (NM).The PM is in charge for combining a user's
IP address with the pseudonym deterministically generated
based on the user's IP address. The NM pairs a user's
pseudonym with the end server. Only if the two managers
are not colluding with each other, the user's connections
remain anonymous to the PM, pseudonymous to the NM
and anonymous to servers that the user connects to.. To do
this user must first connect openly with the PM before
receiving the pseudonym. The PM's one and only
responsibility it to map IP addresses to the pseudonyms.
User then connects to the NM through Tor network
presenting the pseudonym and destined server. The NM
does not know that the IP address of the user, but the
pseudonym provided by the PM guarantees that some
distinctive IP address maps to the pseudonym. User
receives a set of nymble tickets as credential for the end
server. In Existing Nymble no technique to track such users
because of the backward Unlinkability.
ISSN: 2231-5381
user gets another server connection
Server 1
Server 2
Figure 1: The Extended Nymble system
architecture
showing the various modes of Interaction. Note thatusers
interact with the NM and servers though the anonymizing
network
V.
PSEUDO TRACKER BASED
TRACKING:
Pseudo Tracker is developed (as shown in Fig 1) as
part of Pseudonym Manager in our tweak Nymble System.
Pseudo tracker contains identity information of the user and
Rating. A user registered recently is highly rated. This
rating is used to track the users. If a user misbehaves with a
http://www.ijettjournal.org
Page 89
International Journal of Engineering Trends and Technology (IJETT) – Volume 9 Number 2 - Mar 2014
server then the server complaints to Nymble Manager
(NM). NM Complaints the particular Pseudonym to
Pseudonym Manager.Pseudonym Manager sends this
information to Pseudo Tracker, where the rating of
misbehaving user decline depending on no of times user
misbehaved. NM uses rating to blacklist a user for many
linkability windows.
VI.
NYMBLE MANAGER:
After obtaining a pseudonym from the PM, the user
connects to the Nymble Manager (NM) throughout the
anonymizing network, and requests nymbles for access to a
scrupulous server (such asWikipedia). A user’s wishes to
the NM are therefore pseudonymous, and nymbles are
generated using the user’s pseudonym and the server’s
identity. These nymbles are specific to a particular userserver pair. However as long as the PM and the NM do not
get together the Nymble system cannot identify which user
is connecting to what server; the NM knows only the
pseudonym-server pair, and the PM knows only the user
identity-pseudonym pair.
VII.
users through the signature. Drawbacks of Traceable
Signature involve these signatures are traceable and
whenever a user misuses his facilities the manager steps in
and traces the history of the user by the signature.
SECURE CONNECTION :
To provide the requisite cryptographic protection and
security properties, the NM encapsulates nymbles within
nymble tickets. Servers wrap seeds into linking tokens, and
therefore, linking tokens being used to link future nymble
tickets. Whenever a user is blacklisted the pseudonym of
the particular user is send to PM and user gets connected to
another server.
Algorithm 1: NMVerifyPseudonym
Input: {pnym,w}
Output: {true or false}
1 Extract verifyKeyPM1…n from keys in nmState
2 (nym,σnym) := pnym
3 return σnym == RingSig:Verify(nym|| || w,
verifyKeyPM1…n)
Traceable Signatures
In this mechanism, the data can now be signed
like the documents of paper. The electronic signatures [10]
can be assigned to each user to put them on their messages
instead of names and the encoded message will also
contain their signature so the receiver will have the
authentication about the sender without knowing the IP
address of the user or any other identity related information
about him. On the other hand there are group signatures too
which a group or a network can use to identify itself and its
ISSN: 2231-5381
Table 1. Who trusts whom to be how for what guarantee
Cryptographic primitives
Nymble uses the subsequent edifice blocks
i.
Secure cryptographic hash functions. These are
oneway and collision-resistant functions that
resemble random oracles. Denote the range of the
hash functions by H.
ii.
Secure message authentication (MA). These
consist of the key generation (MA.KeyGen), and
the message authentication code (MAC)
computation (MA.Mac) algorithms. Denote the
domain of MACs by M.
iii.
Secure symmetric-key encryption (Enc). These
consist of the key generation (Enc.KeyGen),
encryption (Enc.Encrypt), and decryption
(Enc.Decrypt) algorithms. Denote the domain of
ciphertexts by!
iv.
Secure digital signatures (Sig). These consist of
the key generation (Sig.KeyGen), signing
(Sig.Sign), and verification
v.
(Sig.Verify) algorithms. Denote the domain of
signatures.
VIII.
TIME
While a user’s access within a time period is tied to a single
nymble ticket, the use of different nymble tickets across
time periods grants the user anonymity between time
periods. Smaller time periods provide users with higher
rates of anonymous authentication, whilelonger time
periods allow servers to rate-limit the number of
misbehaviors from a particular user before he or she is
blocked. For example, T could be set to five minutes,
andW to one day (and thus, L ¼ 288). The linkability
window allows for dynamism since resources such as IP
addresses can get reassigned
http://www.ijettjournal.org
Page 90
International Journal of Engineering Trends and Technology (IJETT) – Volume 9 Number 2 - Mar 2014
IX.
DATASTRUCTURES AND MODULES
Nymble uses several important data structures,
and we divide them into the following 4 modules:
Module 1: Generation of pseudonym
The PM issues pseudonyms to users. A pseudonym pnym
has two components nym and mac: nym is a pseudorandom
X.
PERFORMANCE ANALYSIS :
Multiple Link ability: With multiple likability
windows, Nymble construction still has Accountability and
also Nonframeability because each ticket is valid for and
only for a specific linkability window; it still has
Anonymity because pseudonyms are an output of a
collision-resistant function that takes the likability window
as input
Fig 2. Evolution of seeds and nymbles. Given seedsi.
it is easy to Compute nymblei, nymblei+1..nymbleL, but
not nymble*, nymblei……., nymblei-1.mapping of the
user’s identity (e.g., IP address),7 the linkability window w
for which the pseudonym is suitable, and the PM’s secret
key nymKeyP ; mac is a MAC that the NM uses to verify
the integrity of the pseudonym.
Algorithm. PMCreatePseudonym
Input: (uid,w) € H * _
Persistent state: pmState € Sp
Output: pnym € P
1: Extract nymKeyP ; macKeyNP from pmState
2: nym :¼ MA:Mac(uid||w, nymKeyP )
3: mac :¼ MA:Mac(nym||w, macKeyNP)
4: return pnym :¼ (nym, mac)
Module 2: Generation of nymble
Nymble, a pseudorandom number, acts the role of an
identifier for a particular time period. Nymbles (presented
by a user) across periods are unlinkable unless a server has
blacklisted that user. Nymbles are presented as part of a
nymble ticket, as described next. The seed for the next time
period (seednext) is computed from the seed for the current
time period (seedcur) as seednext ¼ f(seedcur):
Algorithm: NMVerifyTicket
Input: (sid, t, w,ticket) € H * _2 * T
Persistent state: svrState
Output: b € (true; false)
1: Extract macKeyN from keys in nmState
2: (. , nymble, ctxt, macN, macNS ) := ticket
3: content := sid||t||w||nymble||ctxt
4: return macN =? MA:Mac(content, macKeyN)
ISSN: 2231-5381
Figure 3: Comparison results with pseudo
with time efficiency results.
.
frames
As shown in the above figure similarity results of
each Nymble client associated with Nymble server is
obtainable in the component process of the anonymizer
network for individual progress of each client results with
time comparison.
Blacklist Ability: An honest PM and NM will issue a
alliance of unique users at most valid credentials for a
given server. Nymble Manager can issue valid tickets, and
for any given time period, the coalition has at most valid
tickets, thus making at most connections in any time period
irrespective of server’s blacklisting. It is enough to show
that if each of the users has been blacklisted in some
previous time period, the alliance cannot authenticate in the
time period.
XI.
IMPLEMENTATION AND
EXPERIMENTAL SETUP:
Network simulator tool can be used to implement the
above system due to its in built properties and
characteristics. Assume that the PM and NM will not be
compromised at any cost. The PM and NM can be
implemented as hosts or servers. In this system PM and
NM are to be implemented as servers. The system requires
2.2GHz Intel Pentium Dual-Core with 4GB RAM
http://www.ijettjournal.org
Page 91
International Journal of Engineering Trends and Technology (IJETT) – Volume 9 Number 2 - Mar 2014
XII.
CONCLUSION:
We have proposed a comprehensive credential system
called tweak Nymble, which can be used to add a layer of
accountability to any publicly known anonymizing
network. Servers can blacklist misbehaving users for a
period of time while maintaining their privacy, and it is
seen how these properties can be attained in a way that is
practical, efficient, and sensitive to needs of both users and
services. Hope that this proposed work will increase the
mainstream taking of anonymizing networks such as Tor,
which has thus far been completely blocked by several
services because of users who abuse their anonymity.
ACKNOWLEDGMENT
We would like to thank Dr.B.Bharathi, Head of the
Department, Department of Computer Science and
Engineering and MS.VijiAmuthaMary for her all
encouragement and support.
REFERENCES:
1.
Patrick P. Tsang, Apu Kapadia, Member, IEEE, Cory
Cornelius, and Sean W. Smith “Nymble: Blocking
Misbehaving Users in Anonymizing Networks” IEEE
transactions on
dependable and secure computing, vol. 8,
no. 2, march-April 2011.
2.
D. Chaum and E. van Heyst, “Group Signatures,” Proc. Int’l
Conf. Theory and Application of Cryptographic Techniques
(EUROCRYPT), pp. 257-265, 1991
3.
Edward J. Schwartz. Contractual Anonymity. Master’s
thesis, Carnegie Mellon University,The Information
Networking Institute, Pittsburgh, Pennsylvania, USA, May
2009.
4.
Zi Lin and Nick Hopper. Jack: Scalable Accumulator-based
Nymble System. In Keith Frikken, editor, Proceedings of
WPES 2010, pages 53–62. Association for Computing
Machinery (ACM) Press, New York, NY, USA, October
2010.
5.
Jason E. Holt and Kent E. Seamons. Nym: Practical
Pseudonymity for Anonymous Networks. Technical Report
2006-4, Brigham Young University, Internet Security
Research Lab, Provo, Utah, USA, June 2006.
6.
R. Dingledine, N. Mathewson, and P. Syverson. Tor: The
Second-Generation Onion Router. In Usenix Security
Symposium, pages 303–320, Aug. 2004
ISSN: 2231-5381
http://www.ijettjournal.org
Page 92