1 2
advertisement
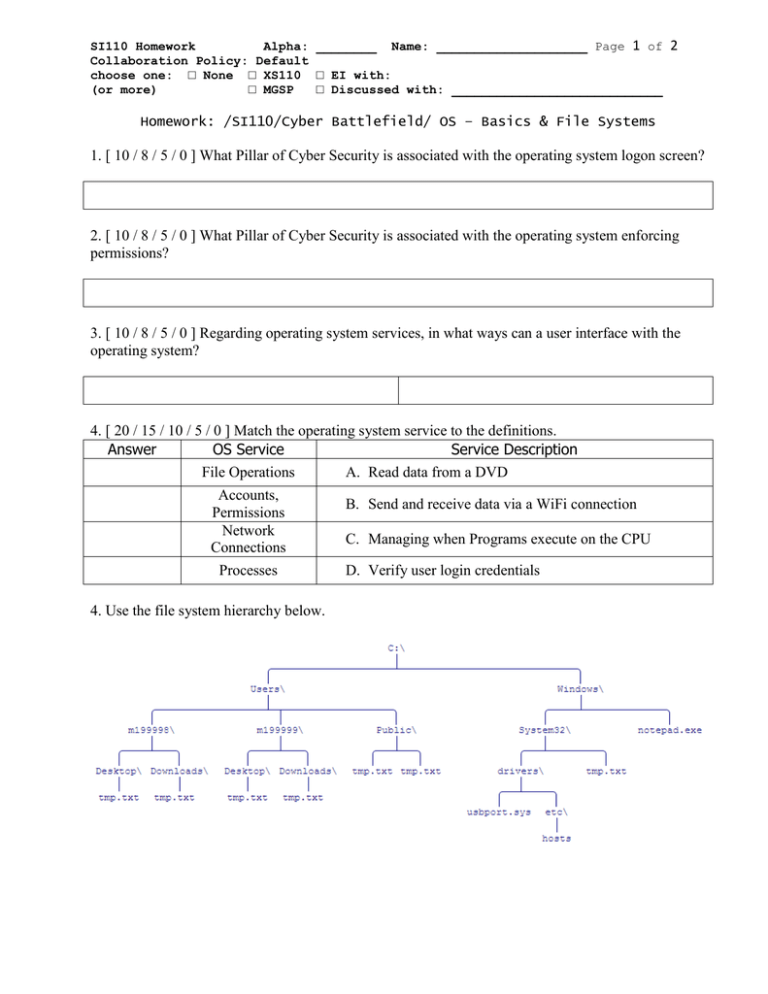
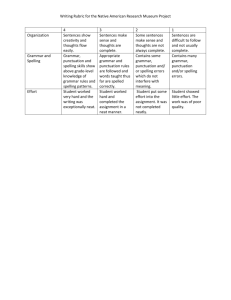
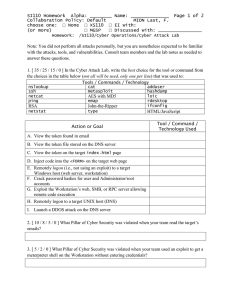
SI110 Homework Alpha: ________ Name: ____________________ Page 1 of Collaboration Policy: Default choose one: □ None □ XS110 □ EI with: (or more) □ MGSP □ Discussed with: ____________________________ 2 Homework: /SI110/Cyber Battlefield/ OS – Basics & File Systems 1. [ 10 / 8 / 5 / 0 ] What Pillar of Cyber Security is associated with the operating system logon screen? 2. [ 10 / 8 / 5 / 0 ] What Pillar of Cyber Security is associated with the operating system enforcing permissions? 3. [ 10 / 8 / 5 / 0 ] Regarding operating system services, in what ways can a user interface with the operating system? 4. [ 20 / 15 / 10 / 5 / 0 ] Match the operating system service to the definitions. Answer OS Service Service Description File Operations A. Read data from a DVD Accounts, Permissions Network Connections Processes 4. Use the file system hierarchy below. B. Send and receive data via a WiFi connection C. Managing when Programs execute on the CPU D. Verify user login credentials SI110 Homework Collaboration Policy: Default Page 2 of 2 a. [ 10 / 8 / 5 / 0 ] Circle the file C:\Windows\System32\tmp.txt on the diagram. b. [ 10 / 8 / 5 / 0 ] What is the full path name for the file hosts shown in the diagram? c. [ 10 / 8 / 5 / 0 ] Draw a box around the files that COULD NOT exist if this were an actual file system on a hard disk drive. d. [ 20 / 15 / 5 / 0 ] Explain why the files in Question 5.c. could not exist in an actual file system; i.e. what is being violated from the perspective of the file system. Use complete sentences, spelling and grammar count. Use complete sentences, spelling and grammar count.