Solutions to Practice Problems RB RA RD
advertisement
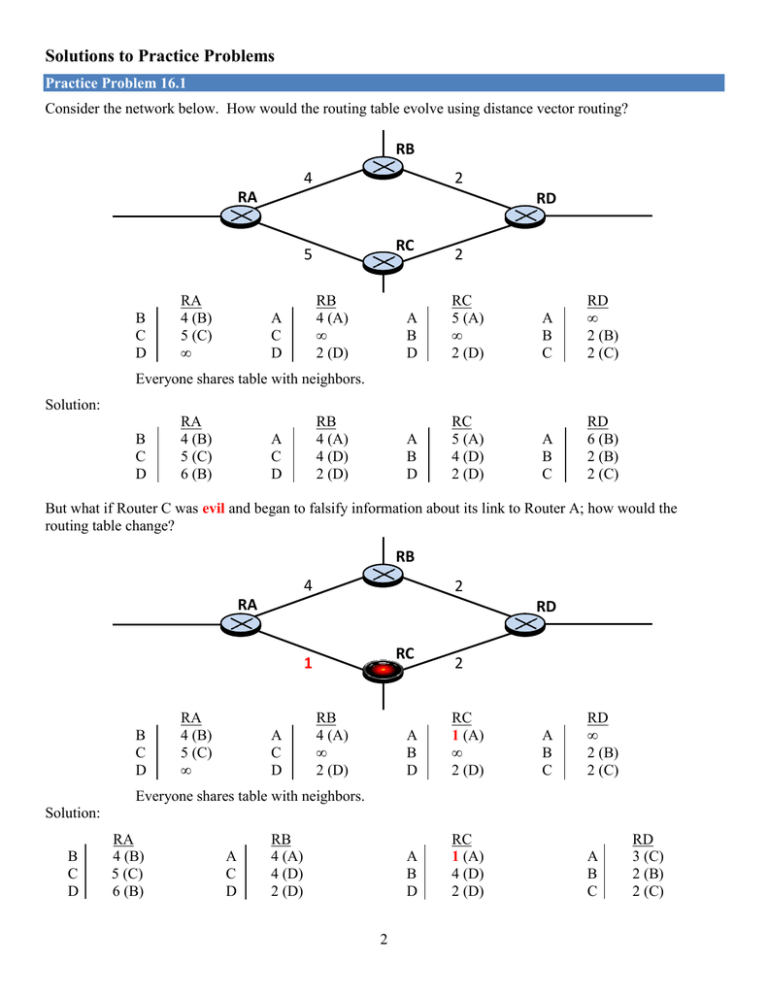
Solutions to Practice Problems Practice Problem 16.1 Consider the network below. How would the routing table evolve using distance vector routing? RB 4 2 RA RD RC 5 B C D RA 4 (B) 5 (C) ∞ RB 4 (A) ∞ 2 (D) A C D 2 A B D RC 5 (A) ∞ 2 (D) A B C RD ∞ 2 (B) 2 (C) A B D RC 5 (A) 4 (D) 2 (D) A B C RD 6 (B) 2 (B) 2 (C) Everyone shares table with neighbors. Solution: B C D RA 4 (B) 5 (C) 6 (B) RB 4 (A) 4 (D) 2 (D) A C D But what if Router C was evil and began to falsify information about its link to Router A; how would the routing table change? RB 4 2 RA RD RC 1 B C D RA 4 (B) 5 (C) ∞ A C D RB 4 (A) ∞ 2 (D) 2 A B D RC 1 (A) ∞ 2 (D) A B D RC 1 (A) 4 (D) 2 (D) A B C RD ∞ 2 (B) 2 (C) Everyone shares table with neighbors. Solution: B C D RA 4 (B) 5 (C) 6 (B) A C D RB 4 (A) 4 (D) 2 (D) 2 A B C RD 3 (C) 2 (B) 2 (C) What does this mean for all of Router D’s traffic destined for Router A? Solution: All of Router D’s traffic destined for Router A will go through Router C instead of Router B. More importantly, why would Router D’s traffic go through Router C instead? Solution Router C manipulated the network by falsifying the information about the distance between it and Router A. Practice Problem 16.2 What primary pillar of information assurance is violated in each thing Router C can do once it is in the middle of Router D and Router A? (a) The ability to observe traffic violates: Solution: Confidentiality (b) The ability to change traffic violates: Solution: Integrity (c) The ability to stop traffic violates: Solution: Availability Practice Problem 16.3 Construct the routing table for Router A. 3 Solution: 192.168.65.0 Practice Problem 16.4 What is the first and last IP address of the 4.4.5.0/24 network where the webserver is located? (a) First Address: Solution: 4.4.5.1 (not counting the network address) (b) Last Address: Solution: 4.4.5.254 (not counting the broadcast address) Looking at Router A’s table, what network ID and mask should the evil instructor choose? Other options? Yes! Target’s Network Target’s IP Address Attacker’s Lie 4 . 4 . 5 . 0 0 0 0 0 0 1 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0 1 0 1 0 0 0 0 0 0 0 0 4 . 4 . 5 . 155 0 0 0 0 0 1 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0 1 0 1 1 0 0 1 1 0 1 1 4 . 4 . 5 . 144 0 0 0 0 0 1 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0 1 0 1 1 0 0 1 0 0 0 0 What is the first and last address of the false network the evil instructor will advertise? (a) First Address: Solution: 4.4.5.145 (b) Last Address: Solution: 4.4.5.158 Does the IP address of the webserver fall within the IP address block that the evil instructor will advertise? Solution: Yes 4 Practice Problem 16.5 What will Router A’s routing table look like, once it hears the lie about the fake network from Router B? 192.168.65.0 Thus, whenever a student sends a packet destined for the webserver at 4.4.5.155, where will Router A forward their packet? Will the EC310 students ever be able to reach the course web page? No, all traffic will be forwarded to Router B because it is advertising a more specific network prefix. 5 Practice Problem 16.6 Briefly describe two technical solutions to protect against false route injection and identify who is responsible for implementing them. Solution #1: Plaintext-password. Added to all LSPs so each route can authenticate the information they send. The Network Administrator would be responsible for implementing this. Solution #2: Passive interfaces. Once an interface is set as passive, the router will ignore all routing information sent over that interface. The Network Administrator would be responsible for implementing this. 6







