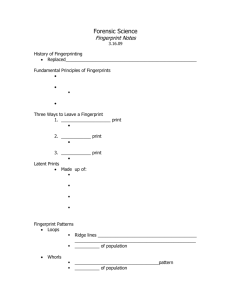
Fingerprint Analysis and Representation
advertisement

Fingerprint Analysis and
Representation
Handbook of Fingerprint Recognition
Chapter III Sections 7-10
Direct Gray-Scale Minutiae Detection in
Fingerprints
D. Mario and D. Maltoni, IEEE Transactions on Pattern
Analysis and Machine Intelligence, vol.19, no.1,pp. 2739, 1997.
Presentation by: Xavier Palathingal
Fingerprint Analysis and
Representation
Handbook of Fingerprint Recognition
Chapter III Sections 7-10
Outline
Enhancement
Minutiae Detection
Binarization based methods
Direct gray-scale extraction
Minutiae Filtering
Structural post-processing
Minutiae filtering in the gray-scale domain
Estimation of Ridge Count
Enhancement
Performance depends on quality of images
Ideal fingerprint
Degradation types – ridges are not continuous, parallel
ridges are not well separated, cuts/creases/bruises
Leads to problems in minutiae extraction
Enhancement
For each fingerprint image, the fingerprint areas
resulting from segmentation can be divided into:
Well-defined region
Recoverable region
Unrecoverable region
Enhancement Algorithms
Goal – to improve the clarity of the ridge structure
in the recoverable regions and mark unrecoverable
regions as too noisy for further processing
Input – a gray-scale image
Output – a gray-scale or binary image depending
on the algorithm
Effective initial steps - Contrast stretching,
Histogram manipulation, Normalization, Wiener
Filtering
Normalization approach [Hong,
Wan, Jain (1998)]
Determines the new intensity value of each pixel
as,
m and v - image mean and variance
m0 and v0 - desired values after normalization
Pixel-wise operation, does not change the ridge
and valley structures
Contextual Filters
The most widely used technique for fingerprint image
enhancement
Conventional image filtering – a single filter is used
for convolution throughout
Contextual filtering - filter characteristics change
according to local context
Several types of contextual filters proposed
Indented behavior – 1)provide a low-pass
[averaging] effect along the ridge direction.
2)perform a band pass [differentiating] in the
direction orthogonal to the ridges
Method proposed by O’Gorman and
Nickerson
A mother filter defined based on-minimum and maximum
ridge width, minimum and maximum valley width.
Filter is bell-shaped, elongated along the ridge direction,
and cosine tapered in the direction normal to the ridges.
The context is defined only by the local ridge orientation
Once the mother filtered is generated, a set of 16 rotated
versions is derived.
The image enhancement is performed by convolving
each point of the image with the filter in the set whose
orientation best matches the local ridge orientation
Method proposed by Sherlock,
Monro, and Millard
Performed in Fourier domain
The filter is defined in the frequency domain by the
function:
where Hradial depends only on the local ridge
spacing ρ = 1/f and Hangle depends only on local
ridge orientation θ
Both Hradial and Hangle are defined as band-pass filters
and are characterized by a mean value and a
bandwidth
The Fourier transform Pi,i=1,…n of the filters is precomputed and stored
Method proposed by Sherlock,
Monro, and Millard (cont …)
Filtering of an input fingerprint image I is performed as follows:
The FFT(Fast Fourier Transform) F of I is computed
each filter Pi is point-by-point multiplied by F, thus obtaining n filtered image
transforms PFi, i=1,…n (in the frequency domain)
Inverse FFT is computed for each PFi resulting in n filtered images PIi, i=1,…n (in
the spatial domain)
The enhanced image Ienh is obtained by setting, for each pixel [x,y],
Ienh[x,y] = PIk[x,y], where k is the index of the of the filter whose orientation is the
closest to θxy
Method proposed by Hong, Wan, and
Jain
Based on Gabor filters
Gabor filters have both frequency-selective and
orientation-selective properties and have optimal
joint resolution in spatial and frequency domains
A Gabor filter is defined by a sinusoidal plane wave
tapered by a Gaussian
Method proposed by Hong, Wan, and
Jain (cont ..)
The even symmetric two-dimensional Gabor filter
has the following form:
Here, f is the frequency of a sinusoidal plane wave
and σx and σy are the standard deviations of the
Gaussian envelope along the x and y axes
Method proposed by Hong, Wan, and Jain
(cont ..) – Gabor Filter
4 parameters – θ,f,σx,σy
The selection of the values σx and σy involves a tradeoff
A set {gij(x,y) | i=1…n0,1..nf} of filters are priori created and
stored , where n0 is the number of discrete orientations {θi |
i=1,..n0} and nf the number of discrete frequencies {fj| j=1,..nf}
Each pixel [x,y] is convolved, with filter gij(x,y) such that θi is the
discretized orientation closest to θxy and fj is the discretized
orientation closest to fxy
Method proposed by Hong, Wan, and Jain
(cont ..) – Examples
Shows the
application of
Gabor-based
contextual
filtering on
medium and
poor quality
images
Minutiae Detection
Reliable minutiae extraction is extremely
important
Enhancement
Binarization
Thinning
Binarization-based methods
Simplest method - global threshold
Local threshold technique
Fingerprint specific solutions necessary
FBI “minutiae reader” – by Stock and Swonger
Composite approach based on a local threshold and a “slit
comparison” formula that compares pixel alignment along
eight discrete directions
Method proposed by Moayer and Fu
Based on an iterative application of a Laplacian operator
and a pair of dynamic thresholds
At each iteration the image is convolved through a
Laplacian operator and the pixels whose intensity lies
outside the range bounded by two thresholds are set to 0
and 1 respectively
The thresholds are progressively moved towards a unique
value to guarantee convergence
Binarization-based methods
A fuzzy approach – by Verma, Majumdar and Chatterjee
Uses an adaptive threshold to preserve the same number of 1 and
0 pixels for each neighborhood
Image is partitioned into small regions
Each region goes through – smoothing, fuzzy coding of the pixel
intensities, contrast enhancement, binarization, 1s and 0s counting,
fuzzy decoding, and parameter adjusting.
Repeated until number of 1s approximately equals 0s
Method proposed by Coetzee and Botha
Based on the use of edges in conjunction with the gray-scale
image
The ridges are tracked by the two local windows: one in the grayscale image and other in the edge image
Gray-scale domain – binarization with local threshold
Edge-image – a blob-coloring routine is used to fill the area
delimited by the two ridge edges
The resulting image is the logical OR of the two individual binary
images
Binarization-based methods
Approach by Ratha, Chen and Jain
Based on peak detection in the gray-scale profiles along
sections orthogonal to the ridge orientation
A 16x16 oriented window is centered around each pixel [x,y]
The gray-scale profile is obtained by projection of the pixel
intensities onto the central section
Binarization-based methods
Approach by Ratha, Chen and Jain [cont ..]
The profile is smoothed through the local averaging; the
peaks and the two neighboring pixels on either side of each
peak constitute the foreground of the resulting binary image
Binarization-based methods
Domeniconi, Tari and Liang (1998) modeled fingerprint
ridges and valleys as sequences of local maxima and
saddle points
Maxima and saddle points are detected by evaluating
gradient and the Hessian matrix H at each point
The Hessian of a two-dimensional surface S(x,y) is a 2x2
symmetric matrix whose elements are the second-order
derivatives of S with respect to x2,xy and y2
The eigenvectors of H are the directions along which the
curvature of S is extremized
Let p be a stationary point and let λ1 and λ2 be the
eigenvalues of H in p
Then p is a local maximum if λ1 ≤ λ2 < 0 and is a saddle
point if λ1. λ2 < 0
Binarization-based methods
Approach by Tico and Kuosmanen (1999)
A slightly different topological approach
Fingerprint image is treated as a noisy sampling of the underlying
continuous surface
Approximated it by Chebyshev polynomials
Ridge and Valley regions are discriminated by the sign of the
maximal normal curvature of the surface
The maximal normal curvature along any direction d is dTHd
Abutaleb and Kamel (1999)
Used Genetic Algorithms to discriminate ridges and valleys along
the gray-level profile of the scanned lines
The optimization criterion is aimed at increasing the correlation
between adjacent gray-levels along fingerprint sections
Results from different methods
Thinning
Reduces the width of the ridges to one pixel
Skeletons , spikes
Filling holes, removing small breaks, eliminating
bridges between ridges etc.
Thinning
Coetzee and Botha (1993) identify holes and
gaps by tracking the ridge line edges through
adaptive windows and remove them using a
simple blob-coloring algorithm
Hung (1993) uses an adaptive filtering technique
to equalize the width of the ridges
To remove the spikes, Ratha, Chen and Jain
(1995) implement a morphological “open”
operator.
Thinning
Fitz and Green (1996) - removes small lines and dots
both in the ridges and valleys of binary images through
an application of 4 morphological operators on a
hexagonal grid
Luo and Tian (2000) - a two step method. skeleton
extracted at the end of the first step is used to improve
the quality of the binary image based on a set of
structural rules. A new skeleton is extracted from this
improved binary image.
Ikeda et. al (2002) - use morphological operators to
enhance ridges and valleys in the fingerprint binary
image
Minutiae detection
A simple image scan allows the pixel
corresponding to minutiae to be detected
crossing number of a pixel p
Examples of minutiae extraction
Direct gray-scale extraction
Such methods are used to overcome the problems
related to fingerprint binarization and thinning [e.g.
spurious minutiae]
Leung, Engeler, and Frank (1990)
Introduced a neural network-based approach
A multi-layer perceptron analyzes the output of a rank of
Gabor filters applied to the gray-scale image
The image is first transformed into frequency domain
where the filtering takes place;
The resulting magnitude and phase signals constitute
the input to the neural network composed of six subnetworks – each of which is responsible for detecting
minutiae at a specific orientation
A final classifier is employed to combine the intermediate
responses
Direct gray-scale extraction
Maio and Maltoni (1997)
Basic idea – track the ridge lines in the gray-scale
image, by “sailing” according to the local orientation of
the ridge pattern
A ridge line is defined as a set of points that are local
maxima along one direction
The ridge line extraction algorithm tries to locate the
local maximum relative to a section orthogonal to the
ridge direction
A polygonal approximation of the ridge line can be
obtained by connecting the consecutive maxima
Results of minutiae detection
algorithm on a sample fingerprint
Variations of Maio and Maltoni method
Jiang, Yau, and Ser (1999) – proposed μ be dynamically
adapted
Liu, Huang, and Chan (2000) – instead of tracking a
single ridge, the algorithm simultaneously tracks a
central ridge and 2 surrounding valleys
Chang and Fan (2001) – aimed at discriminating the true
ridge maxima in the sections Ω obtained during ridge line
following. For this 2 thresholds are initially determined.
Bolle et. al (2002) - provided a formal definition of
minutiae based on the gray-scale image that allows the
location and orientation of an existing minutia to be more
precisely determined
Minutiae Filtering
Post-processing stage is useful for
removing spurious minutiae [already
present or introduced by previous steps]
Two main post-processing types:
Structural post-processing
Minutiae filtering in the gray-scale domain
Structural post-processing
Xiao and Raafat (1991) identified the most common false
minutiae structures and introduced an ad hoc approach
The underlying algorithm is rule-based
Requires as input – length of the associated ridge(s), the
minutia angle, the number of facing minutiae in a
neighborhood
Structural post-processing
Farina, Kovacs- Vajna, and Leone (1999) introduced some optimized
variants of some previously proposed rules and algorithms
Spurs and bridges are removed based on the observation that in a
“spurious” bifurcation, only two branches are generally aligned whereas the
third one is almost orthogonal to the other two
Short ridges are removed on the basis of the relationship between the ridge
length and the average distance between the ridges
Terminations and bifurcations are then topologically validated: they are
removed if the topological requirements are not fully satisfied
Minutiae filtering in gray-scale domain
A direct minutiae filtering technique reexamines the gray-scale
image in a spatial neighborhood of a detected minutiae with the aim
of verifying the presence of a real minutia
Maio and Maltoni used a shared weight neural network to verify the
minutiae detected by their gray-scale algorithm
The minutiae neighborhoods are normalized with respect to their
angle and the local ridge frequency
Minutiae filtering in gray-scale domain
Then they are passed to a neural network
classifier, which classifies them as termination,
bifurcation and non-minutia
A typical three layer neural network architecture
has been adopted
Estimation of ridge count
ridge count has often been used to increase reliability of
analysis
Ridge count is an abstract measurement of the distances
between any two points in a fingerprint image
Typically used in forensic matching
Summary [of the chapter]
Most of the early work was based on generalpurpose image processing techniques
Recent developments have 2 important
directions:
Focus on optimizing the salient discriminatory
information in fingerprints
Algorithms designed specifically for processing
fingerprints images have been proposed
Direct Gray-Scale Minutiae
Detection in Fingerprints
D. Mario and D. Maltoni, IEEE Transactions on
Pattern Analysis and Machine Intelligence, vol.19,
no.1,pp. 27-39, 1997.
Outline
Introduction
Ridge Line Following
Sectioning and Maximum Determination
Tangent Direction Computation
Stop criteria
Minutiae Detection
Performance Evaluation and Comparison
Conclusion
Introduction
Fingerprints are the most widely used biometric features
Most automatic systems for fingerprint matching are based on
minutiae matching
Minutiae classification is based on 4 classes – terminations,
bifurcations, trifurcations (crossovers) and undetermined
This work is based on a two-class minutiae classification
Introduction
This work is a direct gray scale minutiae detection
approach (i.e. without binarization and thinning )
Reasons for not using binarization and thinning :
Loss of information
Time-consuming
Unsatisfactory on low-quality images
Basic idea – follow the ridge lines on the gray scale
image
A set of starting points is determined
For each starting point, the algorithm keeps following the
ridge lines until they terminate or intersects other ridge
lines
Ridge line following – basic definitions
I be an a x b gray scale image with g gray levels
Gray(i,j) be the gray level of pixel(i,j) of I , i=1,…,a and j=1,…,b
Let z = S (i, j) be the discrete surface corresponding to the image I: S (i, j) =
gray (i, j), i=1,…a, j=1,….b.
Ridge line is defined as a set of points which are local maxima along one
direction
At each step, the algorithm attempts to locate a local maximum relative to a
section orthogonal to the ridge direction
By connecting the consecutive maxima, a polygonal approximation of the
ridge line can be obtained
Ridge line following – algorithm
Starting point : [xc,yc] and starting direction : θc
Computes a new point [xt,yt] at each step moving μ pixels
from the current point [xc,yc] along direction θc
Then it computes a section set Ω as the set of points
belonging to the section segment lying on the xy-plane and
having median point [xt,yt], direction orthogonal to θc and
length 2σ + 1
The new point [xn,yn], belonging to the ridge line, is chosen
among the local maxima of an enhanced version of the set Ω
The point [xn,yn] becomes the current point [xc,yc] and a new
direction θc is computed
Ridge line following – algorithm
(pseudo-code version)
Let (is,js) be a local maximum of a ridge line of I
Φ0 be the direction of the tangent to the ridge
line in (is,js)
Ridge line following algorithm - steps
Sectioning and Maximum
Determination
Sectioning – achieved by intersecting S with a
cutting plane parallel to the z direction
The section set Ω( (it, jt), Φ, σ) centered in (it, jt),
with direction Φ = φc + π/2, and length 2σ + 1
pixels, is defined as,
Sectioning and Maximum
Determination
Difficulty in determining the local maximum of the
section set Ω
volcano silhouette
Sectioning and Maximum Determination
An approach aimed at regularizing the
section silhouette
This makes the determination of the local
maxima more reliable
During the ridge line following, each time a
new section is determined, we regularize
its silhouette by means of two steps:
Local regularization – step 1
Local regularization – step 2
Local regularization - results
Tangent Direction Computation
The simplest approach – based on gradient computation
The gradient phase angle denotes the direction of the
intensity maximum change
Therefore, the direction φc of a hypothetical edge which
crosses the region centered in the pixel (ic, jc), is
orthogonal to the gradient phase angle in (ic, jc)
This method, while being simple and efficient, suffers
from non-linearity due to the computation of the gradient
phase angle
Tangent Direction Computation
Kawagoe and Tojo – for each 2x2 pixel
neighborhood, they make a straight comparison
against four edge templates to extract a rough
directional estimate, which is then arithmetically
averaged over a larger region to obtain a more
accurate estimate
Stock and Swonger – evaluate the tangent
direction on the basis of pixel alignments relative
to a fixed number of reference directions
Tangent Direction Computation
Method used in this work :
Uses a gradient type operator to extract a
directional estimate from each 2 x 2 pixel
neighborhood
Then its averaged over a local window by
least-squares minimization to control noise
Stop Criteria
Exit from interest area
Termination
Intersection
Excessive bending
Minutiae Detection
The main difficulty is of examining each ridge line only
once and locating the intersections with ridge lines
already extracted
To solve this, an auxiliary image T is used
T has the same dimension as that of I, and is initialized
with pixel values set to 0
Every time a new ridge line is extracted from I, the pixels
of T corresponding to the ridge line are labeled by
assigning them an identifier.
Minutiae Detection
The pixels of T corresponding to a ridge line are the pixels
belonging to the polygonal, ε-thick, which links the
consecutive maximum points (in, jn)
The algorithm find minutia searches for a minutia by
following the ridge line nearest to the starting point
Minutia Detection – Algorithm
Minutia detection
The algorithm starts by computing a point (ic, jc)
belonging to the ridge line nearest to the starting point
(is, js).
This operation can be carried out as follows:
Minutia detection
The computation of tangent direction, the sectioning, the
regularization and the determination of the maximum are
performed as in the ridge line following algorithm.
The following figure shows an example:
Minutia Detection
stop criteria revisited
Minutia Detection
The algorithm find minutia enables all the fingerprint
minutiae within a window W to be detected
Figure shows the results obtained by applying this
approach to a sample fingerprint
Performance Evaluation and
Comparison
Performance Evaluation and Comparison
The technique mentioned in this paper (A) and four other
schemes based on binarization and thinning – B, C, D, E
In all approaches , the minutiae detected have been
filtered by removing:
The minutiae belonging to regions where the image contrast is less
than half of the average image contrast
The pairs of termination minutiae which are less than k pixels (k=6)
distant from each other
The sets of bifurcation minutiae (except one minutia for each set)
belonging to a neighborhood with diameter k pixels (k=6)
Performance Evaluation and Comparison
Performance Evaluation and Comparison
Performance Evaluation and Comparison
Conclusions - drawn from the tables
the average error percentage, in terms of dropped and
exchanged minutiae, as produced by proposed
approach is comparable to the errors produced by the
other approaches, although slightly larger.
the average error percentage, in terms of false minutiae,
as produced by proposed approach is considerably
lower than the errors produced by the other approaches.
the average computational time of proposed approach is
considerably lower than the time of the other
approaches.
approach E, whose performance in terms of total error is
comparable with that of proposed approach, is one order
of magnitude slower than our approach.
Performance Evaluation and Comparison
Computational complexity
We assume, for
simplicity, that a
fingerprint pattern is
made up of a set of
straight horizontal
segments, which are
ξ-pixels thick and ξpixels distant from
each other
The elementary operations carried
out at each ridge line following step
Conclusion
A new technique is proposed – based on
ridge line following algorithm
In spite of greater conceptual complexity,
this technique has less computational
complexity than the complexity of
techniques requiring binarization and
thinning